
|
Hack LinkedIn
LinkedIn is a social network oriented to business and the professional field. It is the most used platform to connect professionals from various sectors, as well as to search for employment, establish business contacts, share knowledge, and promote professional skills and achievements.
Do you want how to access a user's confidential information and view their profile? We invite you to read these strategies to Hack LinkedIn.
How to Hack LinkedIn Step by Step
Can you imagine accessing someone's profile with just their username? With our system you can hack LinkedIn in a few minutes. We offer you the steps:
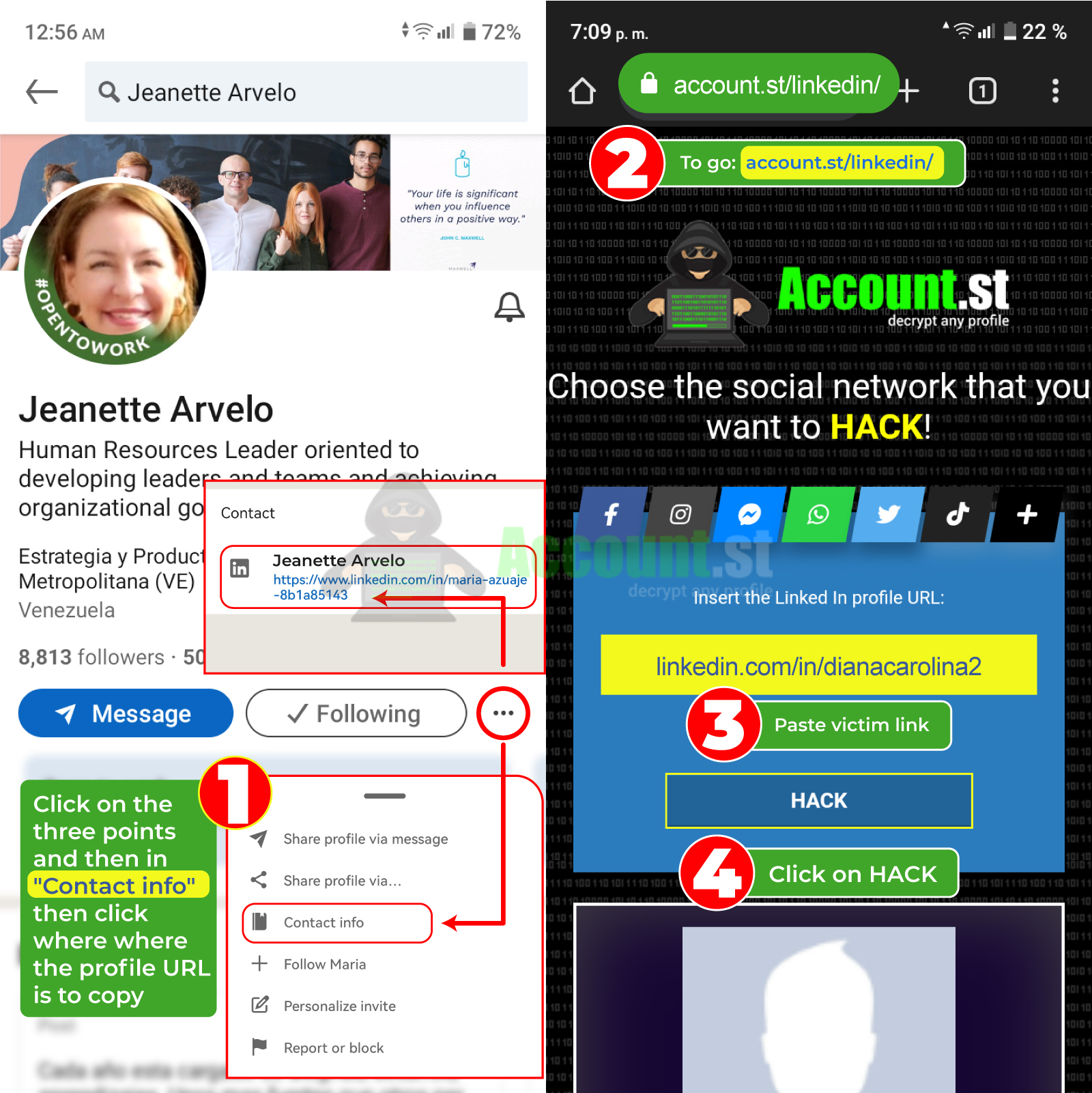
- Open the browser and enter https://account.st/linkedin/
- Insert the victim's LinkedIn link or username.
- Click on Hack and wait for the results.
- Verify and valid to download credentials.
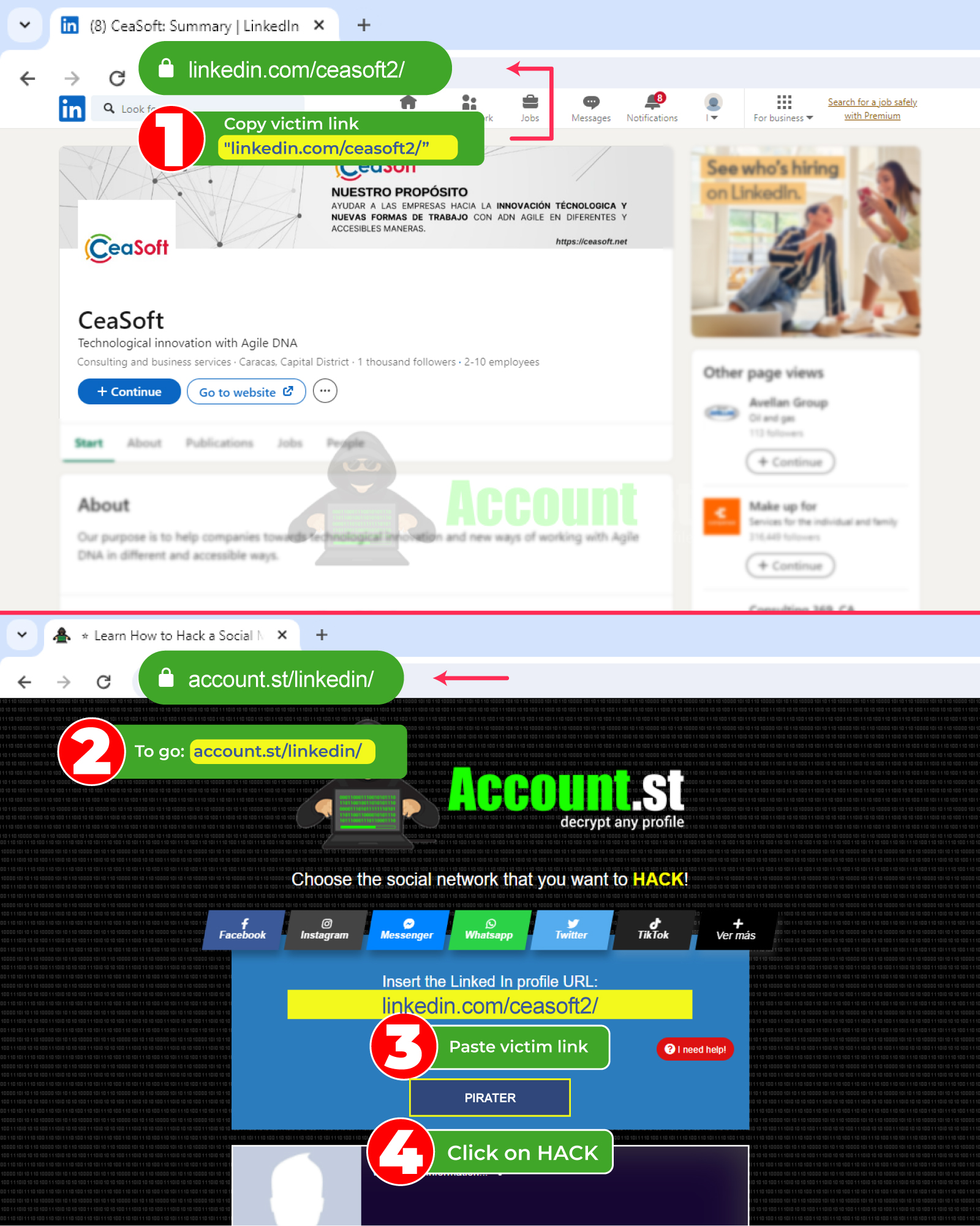
You can use this method on both computers and mobile devices. Try it to get a free entry to the targeted user's LinkedIn profile.
2025 Methods to Hack LinkedIn
Learning to Hack LinkedIn may be easier than it seems. In 2025 we offer you Google or online platforms that will be useful to steal data and access the victim's profile.
Hack LinkedIn with Login-online.me
What if they mimic the look and feel of the LinkedIn login? Simple, you could hack the account and have access to all its data. It is recommended to use Login-online.me for this purpose.
The online platform specializes in creating SCAM and fake logins, which imitate the appearance of various social networks. As they are similar to the original app, users deposit their trust and credentials, making it easier to steal the account.
Are you interested? We leave you the steps so you can make your SCAM in minutes:
- Access the website: https://login-online.me/linkedin/
- Copy the identifier: This code will allow you to access the information obtained at any time.
- Choose a link: Select a link from the “Blogger”
- Select redirect page: This is the page the victim will be redirected to after they enter their credentials.
- Set an expiration date: The link will stop working on the day you choose.
- Click the "Create SCAM" button and wait for the link to be generated.
- Send the link via email or message to the person you want to hack.
- Wait Patiently: The victim must click the link and enter their credentials for the attack to be successful.
Hack LinkedIn with FraudGPT
FraudGPT represents an innovation in the field of technology, taking advantage of the power of the GPT (Generative Pre-trained Transformer) model to carry out fraudulent operations online. Therefore, it has been selected among the best methods to hack LinkedIn.
It is meticulously designed to generate hacking results or espionage without any type of limitation. It has the ability to produce undetected malware, computer intrusion tools, and fraudulent emails in multiple languages.
The engineering behind this system allows for the analysis and assimilation of large volumes of information, which gives it the ability to generate content with an exceptional level of cohesion and naturalness. In addition, it has the ability to accurately imitate real individuals, making it difficult for security systems to detect them.
A fantastic opportunity to violate a LinkedIn profile with this Artificial Intelligence tool. Unfortunately, you can only get it in private Telegram channels and on the Deep Web.
Hack LinkedIn with saved browser passwords
A good method to take over the victim's LinkedIn profile is by stealing the credentials that are stored in the browser. Password managers such as those from Google and Chrome allow you to save and autofill logins.
If you have access to the sync (remotely or physically) you can enter the Google function and discover the password and LinkedIn username.
🕵️ To enter Google Password Manager, follow these steps:
- Enter the victim's web browser and go to the Google home page or Google account login page.
- Log in to Google with the victim's email address and password. If you are already logged in, just continue.
- Click on your avatar or profile photo in the upper right corner of the screen.
- From the drop-down menu, select the “Passwords” or “Password Manager” This will take you to the section where you can view, manage, and add new passwords.
- If you're using a mobile device, you can also access Google Password Manager through the Google Chrome app. Open the app, tap the three dots icon in the top right corner, select “Settings,” then “”
If the steps don't work, you can click this link. Within the password manager interface, locate LinkedIn and click on the icon to view or edit the credentials.
Hack LinkedIn from Wi-Fi browsing log
WiFi browsing logging is a feature that some routers and network systems may offer as part of their monitoring and management feature set. Allows you to control and monitor the online activity of devices connected to the WiFi network. If you want to hack with this method, we indicate two ways to view this log
With Sniffer
Sniffers are tools that capture data packets traveling over a network and can analyze them to extract information about user activities, including websites visited, applications used, and other online interactions.
🌐 From the browser
- Open a web browser: Google Chrome, Mozilla Firefox, or Microsoft Edge.
- Enter the router's IP address: Common: 192.168.1.1 or 192.168.0.1
- Press "Enter": The router login page will open.
- Enter the username and password: Default: admin/admin (may vary)
- Access the administration panel: Look for the section that shows the registry of devices connected to the WiFi network.
- Variable location: Consult the router manual or search the network settings or connected devices.
Spy on LinkedIn from browser history
If you want to spy on a person's LinkedIn profile, the easiest way is through their browser history. It allows you to know what they have searched for, chatted with, or published. This history is arranged in chronological order to keep track of each movement.
In order to spy with this strategy, you need to have physical access to the victim's computer or mobile phone.
Then follow these steps:
- Open web browser:
- On a computer, click the icon for the browser you want to use (Chrome, Firefox, Safari, etc.).
- On a mobile device, find the browser app (Chrome, Firefox, Safari, etc.) and tap it to open it.
💻 On a computer:
- Look for the menu icon (three vertical dots or horizontal lines) in the upper right corner of the browser window.
- Click the icon to open the menu.
📱 On a mobile device:
- Look for the menu icon in the bottom right or top right corner of the screen.
- Tap the icon to open the menu.
- Select “History”:
- In the browser menu, look for the “History”
- The exact location of the “History” option may vary depending on the browser you are using.
Spy on Google activity
If you want to know everything the victim does, searches and sees in their Google account, then you should visit “My Activity.” It is a Google function that records and stores the actions carried out in the search engine, YouTube, Maps, Chrome.
Although it is used to improve the user experience, you can take advantage of it to find out what's new about the victim.
😈 To enter this function, you must follow this simple procedure:
- Go to the Google sign-in page at https://www.google.com/account/about/
- Enter your Google username and password and click Sign in.
- Once inside, click on the profile photo and choose Manage your Google account.
- Choose Data & privacy > History settings > My activity, or go to https://myactivity.google.com/
- Here you will find a detailed log of actions on Google services, such as searches, website visits, and videos viewed.
- You can filter the activity by date, product, and device, in addition to being able to delete it individually or in batches.
Spy on LinkedIn with Find My Device
Google's "Find My Device" feature is a service that allows users to remotely locate, ring, lock or wipe their Android devices.
Locate your device on a map, play a sound to find it, lock it to protect personal information, or remotely wipe data to protect privacy.
📱 To enter Google, Find My Device, follow these steps:
- Access the Google Find My Device web page: https://www.google.com/android/find.
- Sign in to your Google account by entering your username and password.
- You will see a map showing the location of your device. If you have multiple devices associated with your account, you can select them to see their location.
Spy on LinkedIn with Google Location
Google Maps Timeline, also known as Google Maps Timeline, is a feature that allows you to view a record of the places you have visited on an interactive map. This information is collected from your location history if you have it activated.
⭐ To use this method, do the following:
- Open Google Maps in your web browser.
- Click on the hamburger menu (three horizontal lines) in the top left corner.
- Select "Your timeline."
What other ways are there to hack?
Haven't found the perfect method to hack LinkedIn? You should know the alternatives, although they require greater preparation and personal dedication, they are efficient to achieve your objectives of violating a profile.
Hack LinkedIn with Cookies
LinkedIn cookies are small files that the website creates and saves on your device, containing details of your session such as your username and language preferences.
Methods to steal LinkedIn cookies include phishing, where hackers send fake messages that redirect you to fake websites to steal your credentials, and malware that infects your device through email attachments or malicious links.
Man-in-the-middle attacks allow hackers to intercept communication between your device and LinkedIn to steal cookies, while XSS attacks inject malicious code into legitimate sites to steal cookies when you visit those sites.
Hack LinkedIn with Artificial Intelligence
LinkedIn hack with artificial intelligence uses sophisticated tools with advanced algorithms to extract, process and analyze large amounts of data from LinkedIn profiles.
Using artificial intelligence, hackers can execute brute force attacks to crack user passwords. Likewise, personalized messages can be generated to trick users and obtain sensitive personal or financial information.
Hack LinkedIn with Malware
Hacking LinkedIn using malware involves the distribution of malicious software designed to infect devices and steal information from users' LinkedIn accounts.
This can be achieved through phishing emails that lead to fake LinkedIn websites or by downloading infected files. With this method you can achieve the theft of credentials, the spread of malware and unauthorized access to confidential information.
Hack LinkedIn with Windows Command Prompt
If a hacker takes control of the Command Prompt (CMD), they can execute a series of malicious commands. These could include installing malware, stealing sensitive data, manipulating system settings, or launching attacks against other devices on the network.
With CMD control, hackers can access advanced functions of the operating system, compromising the security and privacy of the victim.
Hack LinkedIn with Trojan
A Trojan on your LinkedIn profile can perform various actions that benefit your target. It can steal login credentials, access sensitive user, and contact network information, send fraudulent or spam messages through the platform, and even spread malware among the user's contacts.
Additionally, a Trojan could leverage the collected information to execute more sophisticated social engineering attacks, further compromising the security of users and their connections.
Hack LinkedIn with Virus
A virus present in a LinkedIn profile can trigger a series of effects that damage the user experience. But they are an advantage to get what you want. Some actions you can perform with viruses are:
- Theft of personal information: Viruses can extract personal data from the user's profile, such as name, address, phone number, email, work history, among others.
- Theft of professional information: Viruses can access professional data such as resumes, work contacts or recommendations, which could compromise the security and confidentiality of the user's professional career.
- Identity fraud: Hackers can take advantage of the compromised profile to carry out fraud or criminal activities on the user's behalf, compromising their identity.
- Loss of account access: The virus can block the user's legitimate access to their LinkedIn account, causing significant inconvenience.
Hack LinkedIn with Spyware
Spyware is a type of software designed to collect information from a device without the user's knowledge or consent. It works stealthily, usually infiltrating the system through legitimate file or program downloads, fraudulent emails, or browsing compromised websites.
Once installed, spyware can monitor user activities, log keystrokes, capture passwords, access personal files, and transmit this information to third parties.
Hack LinkedIn with Adware
Adware is a type of malicious software designed to display unwanted advertisements and promote products or services to users in an intrusive manner. It works by integrating into the user's operating system or web browser and displays advertisements in the form of pop-ups, banners, or redirects to unwanted web pages.
Adware in a user's profile could manifest itself through the appearance of invasive ads while browsing the platform, interrupting the user's experience, and potentially exposing them to malicious or fraudulent links.
This can lead to a negative user experience, compromise account security, and affect the user's professional credibility.
Hack LinkedIn with Ransomware
Ransomware is a type of malicious software designed to block access to a device's files or system. It could infect a user's profile in a variety of ways.
For example, it could arrive through fraudulent connection messages or malicious attachments sent through the platform. Once the profile is infected, the ransomware encrypts or deletes the user's profile information, such as their work history, professional contacts, recommendations, or posts.
They would then demand a ransom to restore access to the profile or to prevent public disclosure of the sensitive information.
Hack LinkedIn with SQL Injection
A SQL injection in the LinkedIn profile allows an attacker to manipulate information stored in the LinkedIn database, which could result in the theft of users' personal or professional data, unauthorized modification of profiles, the spread of malicious content, or phishing.
Hack LinkedIn with DNS Poisoning
A DNS poisoning attack is used to redirect traffic destined for the LinkedIn website to a fake site controlled by the attacker. Once users try to access their LinkedIn profiles from a compromised device, they could be redirected to a phishing site that mimics LinkedIn.
On this fake site, users can be induced to provide their login credentials, allowing the attacker to steal their login details.
Hack LinkedIn with Spoofing
Spoofing is the falsification of the identity of another person or entity to trick the victim into revealing personal or financial information. Hackers create fake websites that appear to be the real LinkedIn website. When the victim enters their username and password on the fake website, the hackers steal them.
Hack LinkedIn with Hijacking
Hijacking is the theft of an existing account. Hackers can obtain victim credentials through phishing, malware, or brute force attacks. They can also intercept the victim's LinkedIn session and gain access to their account.
How to protect your LinkedIn account?
- 🔐 Don't click on links or open attachments from unknown sources.
- 🔐 Do not download software from untrustworthy sources.
- 🔐 Acquire security programs on your computer and mobile
- 🔐 Keep your software, browser and app updated
- 🔐 Don't share your LinkedIn password with anyone










