
|
Hack WhatsApp 🕵
Do you want to read WhatsApp messages from a friend, family member or partner?😈 Then you need to learn techniques to hack this messaging platform. Don't worry because the procedures are easier than you think. In this post we will teach you how to hack a WhatsApp account in minutes.
How to Hack WhatsApp Step by Step
By just adding a few simple details and clicking you can hack a WhatsApp account. Account.st It is the best service to learn and hack social networks. It has a very simple interface, we explain the steps:
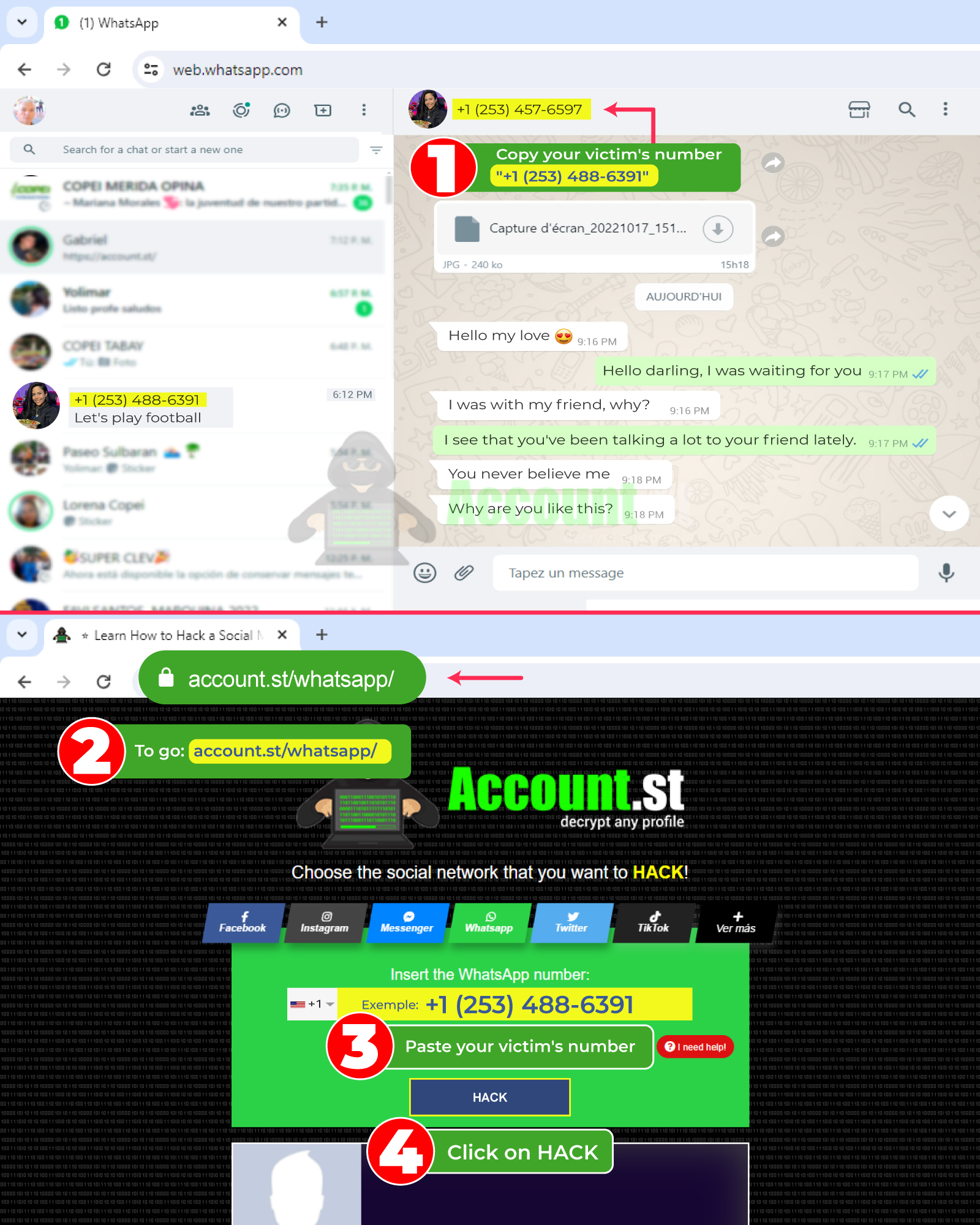
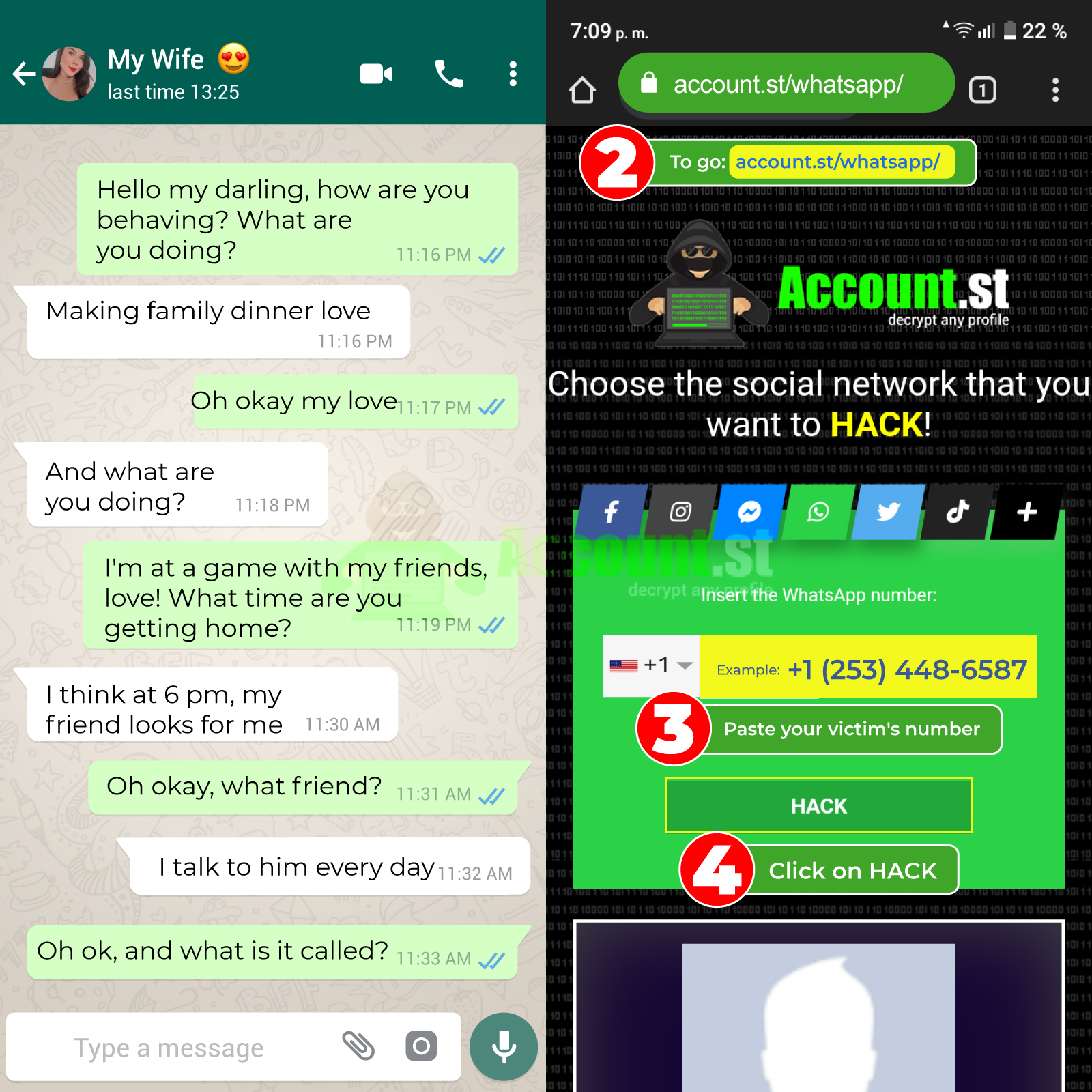
- Open the website: https://account.st/whatsapp/
- Copy and paste the victim's phone number into the box provided.
- Click on the “hack” button
- Perform verification and download the data obtained
That's how easy it is to hack WhatsApp with our platform. Do you dare to try them? Remember that you can tell us about your experience.
2025 Methods to Hack WhatsApp
In 2025, the methods to breach a WhatsApp account have evolved exponentially. From Google's online tools and other services you can have the access you need to know the victim's information. Let's see what they are:
Hack Instagram with Login-online.me
Do you know anything about phishing? It is a technique that consists of sending emails or text messages that appear to come from a legitimate company or institution. The goal is for the victim to click on a link or provide personal information.
Although it may seem like a complex task, Login-online.me. You can run your own deception campaign using a SCAM. This system is based on the creation of fake web pages that imitate well-known platforms or social networks. This way you can trick the user into entering their personal data, such as username, password, and email address.
⭐ Steps to follow:
- Go to the website: https://login-online.me/
- Search for the social network that you want to imitate, in the interface you will see an identifier that you must save and then access the data obtained
- Indicate the Blogger or link among the available options
- If you are a premium user you can add a link to redirect the victim
- Add the expiration date and click on create SCAM
- Send the link to the person to hack and wait for the results
It is a simple method to hack WhatsApp, as a strategy we can recommend that you send an attractive message, posing as the platform or offending a service/discount.
Recover my Facebook account
Another way to access it is through the Facebook recovery option. The procedure is very simple:
- Accede to https://www.facebook.com/hacked, this is the specific Facebook page dedicated to helping users who have been hacked.
- Click on “Recover your account”: you will see a button or link that will take you to start the account recovery process.
- Enter your login information: Facebook will ask you to enter your email address, phone number, or username associated with your hacked account. If you do not remember this information, follow the instructions provided to try to recover it.
- Verify your identity: Facebook may ask you to verify your identity to make sure you are the rightful owner of the account. This may involve answering security questions, such as your date of birth, names of friends on your list, or providing a photo of your government ID.
Hack Instagram with FraudGPT
FraudGPT is a generative artificial intelligence (AI) model used for the creation of malicious content such as phishing emails and fake websites. It is known as the "evil twin" of ChatGPT.
With this tool you can create malicious content, FraudGPT has the ability to generate highly convincing phishing emails, fake websites, undetectable malware, hacking tools and social engineering content.
This service is offered by subscription on Dark Web Telegram channels, allowing access in exchange for a fee.
Hack WhatsApp with saved browser passwords
View saved passwords in the browser means accessing a list of passwords that the victim has previously stored on it. This allows you to quickly view and manage login credentials for websites or apps like WhatsApp.
It is a feature that makes it easy to access online accounts, but requires authentication to keep your data safe. Here we explain how you can access passwords from Chrome and Safari:
🌐 Google Chrome:
- Open Chrome.
- Click on the three vertical dots in the upper right corner.
- Select “Settings”.
- In the left panel, select “Autofill.”
- Click “Passwords.”
- You will be shown a list of all the passwords saved in Chrome.
🌐 Safari:
- Open Safari.
- From the “Safari” menu, choose “Preferences.”
- Click the “Autofill” tab.
- Select “Passwords” to view the list of passwords saved in Safari.
Additionally, you can take advantage of Google Password Manager, a free tool that ensures secure storage and management of your passwords. To access your passwords saved in Google Password:
- Sign in with the victim's Google account.
- Go to the Google Password website: https://passwords.google.com/.
- If prompted, sign in with your Google account.
- You will see a list with all your saved passwords.
Hack WhatsApp from Wi-Fi browsing log
A strategy to hack WhatsApp during 2025 is to view the Wi-Fi browsing log. This involves accessing the internet activity of devices connected to the wireless internet service.
This log includes the victim's web pages, applications, downloads, documents, IP addresses. There are two main methods to access this registry:
💪🏼 Access the router administration panel:
- Log in through a web browser using the router's IP address.
- You will need login credentials or physical access to the router
- Find a section dedicated to browsing log
Spy on WhatsApp from browser history
If the victim uses the web version of WhatsApp, it is the perfect opportunity to exploit logins. For this you must enter the browser history to look for an entry that allows you to fulfill your fiancé.
Don't know where to find the history? We show you the steps for mobile and computer:
💻 In the computer
- Open the web browser.
- Look for the history icon. This icon is usually a clock or a book.
- Click the history icon. A new window or tab will open with your browsing history.
- In history, you can see the websites you have visited, the date and time of the visit, and the number of times you have visited each website.
📱 On mobile:
- Open the web browser.
- Tap the browser menu. This menu is usually represented by three vertical dots or horizontal lines.
- Select the “History” option. A new window or tab will open with your browsing history.
- You will be able to see a list of the websites you have recently visited on your mobile device.
Spy on Google activity
Google activity refers to the information and logs generated by the use of the various Google services and products. This activity can help you learn more information about the victim and take advantage of it to hack WhatsApp.
💪🏼 We explain the steps so you can spy with this Google function:
- Access the victim's Google account or from their devices.
- In the left panel, select “Data & Privacy.”
- Under “History Settings,” click “My Activity.”
- You'll see a detailed list of all your Google activity, organized chronologically.
- Product: Google Chrome, YouTube, Google Maps, among others.
- Theme: Searches, location history, voice activity, etc.
- Date and time: Specify a date range to display the activity.
- Delete activity: Delete individual items or items grouped by product, topic, or time period.
- Turn off activity history: Stop Google from recording your activity so it is not stored.
Spy on WhatsApp with find my device
Find My Device, is a free service provided by Google that offers a variety of features to help if your Android device is lost or stolen. With this tool, you can spy on the exact location of the victim's mobile. Additionally, if the device is nearby but you can't find it, you can make it make a sound to help you find it.
🌐 To access Google “Find My Device,” follow these steps:
- In a web browser, visit https://www.google.com/android/find
- On an Android device, open the Find My Device app.
- Sign in with the Google account associated with the device you want to locate.
- Once logged in, you'll see the location of the target device on a map.
⭐ Additional options:
- Ring your device to help you find it.
- Lock the device with a message and a contact number in case of loss.
- Erase device data irreversibly to protect your information.
Spy on WhatsApp with Google Location
One last function to spy on a WhatsApp account is timeline, integrated into Google Maps, records the locations of your mobile device. It works by collecting location data from your Android or iOS device, continuously sent to Google if you have Location History enabled.
Google stores this data and presents it on a chronological map in the Google Maps app, showing each location visited with details such as date, time and duration. To spy, open https://www.google.com/maps/timeline and enter the victim's account to track their location.
What other ways are there to hack?
We show you other ways to hack a WhatsApp account, these require better preparation and training. Even so, they are effective for reading the messages on this platform.
Hack WhatsApp with Cookies
One of the ways to access WhatsApp is by stealing cookies, files with information and account data: name, phone number and personal preferences. If you use this method you can impersonate the user, send fraudulent messages to their contacts.
That is, accessing the WhatsApp account without authorization, allowing you to see all the information without limitations.
Hack WhatsApp with Artificial Intelligence
The advancement of artificial intelligence has given rise to new hacking methods on WhatsApp. Hackers can use AI to create highly personalized phishing attacks, generating deceptive messages that appear to come from trusted sources.
In addition, AI can be used to impersonate your voice, deceiving your contacts and obtaining confidential information. Advanced malware can also be developed that is difficult to detect and remove.
Hack WhatsApp with Malware
Malware is specialized software that can be used to steal personal, financial and banking data from your device. It may compromise the normal functioning of WhatsApp.
It is usually used to spy on activities on WhatsApp, accessing conversations and other sensitive data.
Hack WhatsApp with Windows Command Prompt
From Windows you can also compromise a WhatsApp account or at least steal important data from the victim. The Windows Command Prompt or CMD allows you to access confidential files stored on your computer.
With this you can take full control of the device, performing actions on your behalf and compromising your online privacy and security.
Hack WhatsApp with Trojan
Trojan is a common form of hacking on WhatsApp, where hackers can steal users' personal, financial and banking information. Once installed on the device, the Trojan allows the attacker to access the victim's WhatsApp account, so it is possible to read their messages and gain access to sensitive data.
The Trojan can spread to other devices on the same network, increasing its range and potential damage.
Hack WhatsApp with Virus
A virus is software designed to infect mobile devices and compromise the WhatsApp account. These viruses can spread through text messages, malicious links, infected attachments, or other forms of interaction within the platform.
Once the device is infected, the virus can cause a series of problems such as theft of personal data, spying on conversations, sending unwanted messages to contacts, damaging the device's operating system, and more.
Hack WhatsApp with Spyware
Spyware can capture and record text messages, voice calls, shared media files, and even the user's location without their knowledge or consent.
The main purpose of WhatsApp spyware is to collect private and sensitive user information for malicious purposes, such as identity theft, blackmail, personal espionage, or collecting data to be sold to third parties.
Hack WhatsApp with Adware
Adware displays unwanted ads on user's device and tracks your online activity. In addition to being intrusive, it can steal personal and financial information, making it a simple strategy to hack a WhatsApp account.
Hack WhatsApp with Ransomware
Ransomware is one of the best forms of hacking due to its destructive capacity and encryption of user files. The goal is to block access to the user's data and then demand a ransom to unlock it.
If the user does not pay the ransom, they risk permanently losing their files. In addition to data loss, ransomware can damage the affected device, compromising its operation.
Hack WhatsApp with SQL Injection
It is a technique used to manipulate databases by inserting custom SQL code into the inputs of a web application. If a WhatsApp application or other service uses this hacked database, your data could be manipulated and you would lose information or control of the app.
Hack WhatsApp with DNS Poisoning
This technique involves manipulating Domain Name System (DNS) responses to redirect traffic from a legitimate website to a malicious one controlled by an attacker.
If an attacker poisons the DNS used by WhatsApp, they could redirect user requests to malicious servers and thus intercept, modify or steal communication data.
Hack WhatsApp with Spoofing
Better known as identity or phone number spoofing. It involves impersonating another person or falsifying the identification of the sender of a message.
Attackers can use spoofing techniques to send messages that appear to come from a known contact or even from the WhatsApp service itself, with the goal of tricking users into revealing sensitive information or downloading malware.
Hack WhatsApp with Hijacking
Finally, the hijacking attack represents a good option to hack WhatsApp, it consists of hijacking a login to the app. This can be through the web version or by stealing the user's login credentials,
How to protect your WhatsApp account?
- 🔐 Enable two-step verification: Activate two-step verification in WhatsApp settings.
- 🔐 Keep the app updated: Regular updates typically include security patches that fix known vulnerabilities and improve protection against potential attacks.
- 🔐 Protect your device with a password or PIN: Be sure to physically protect your mobile device with a password, PIN, or secure unlocking method.
- 🔐 Do not share your verification code: This code is vital to verify your identity and access your account.
- 🔐 Avoid responding to verification requests from unknown or suspicious numbers.










