Trace mobile
Trace any mobile, anywhere in the world, quickly and easily without having to download anything. Locate any mobile device with just the number, without installing anything.

Leaving no traces
100% guaranteed.

|
Track Mobile 🕵
Is it possible to track a cell phone? Yes, you can spy and know the location of other user's devices. There are applications and services designed for this purpose.
Although they are designed for parental control or location in case of theft. You can take advantage of them for your hacking and espionage purposes.
How to Track a Cell Phone Step by Step
With our system, you can know the location of a mobile device in real time with just a few clicks. Enter the phone number and get the precise location of the device, as accurate as a GPS.
The service will not cost you a cent, if you want to learn how to use it you must follow this step by step:
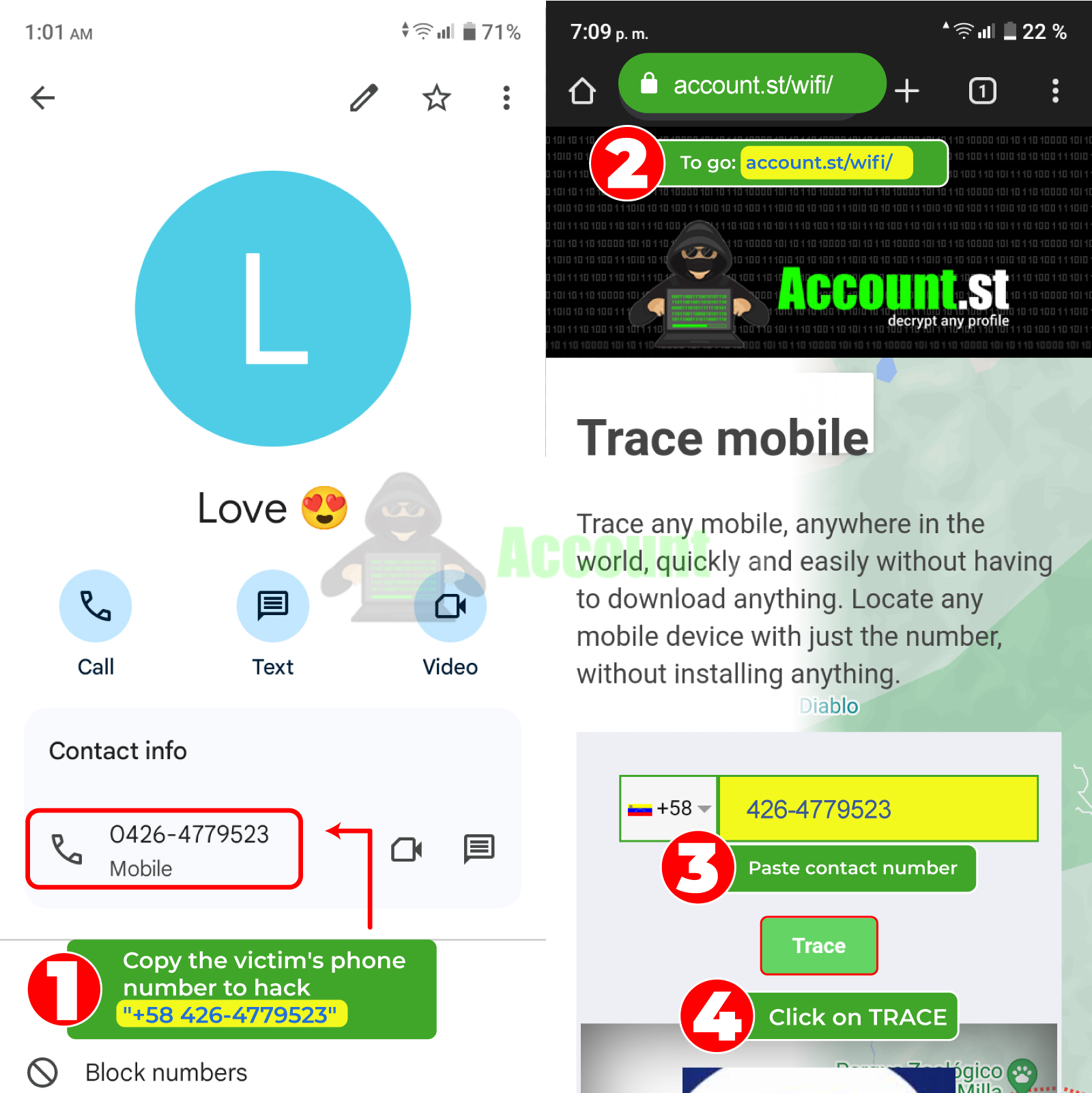
- Copy the victim's phone number.
- Go tohttps://account.st/track-mobile/ .
- In the text bar, select the area code and paste the contact number.
- Click on the “Trace” button.
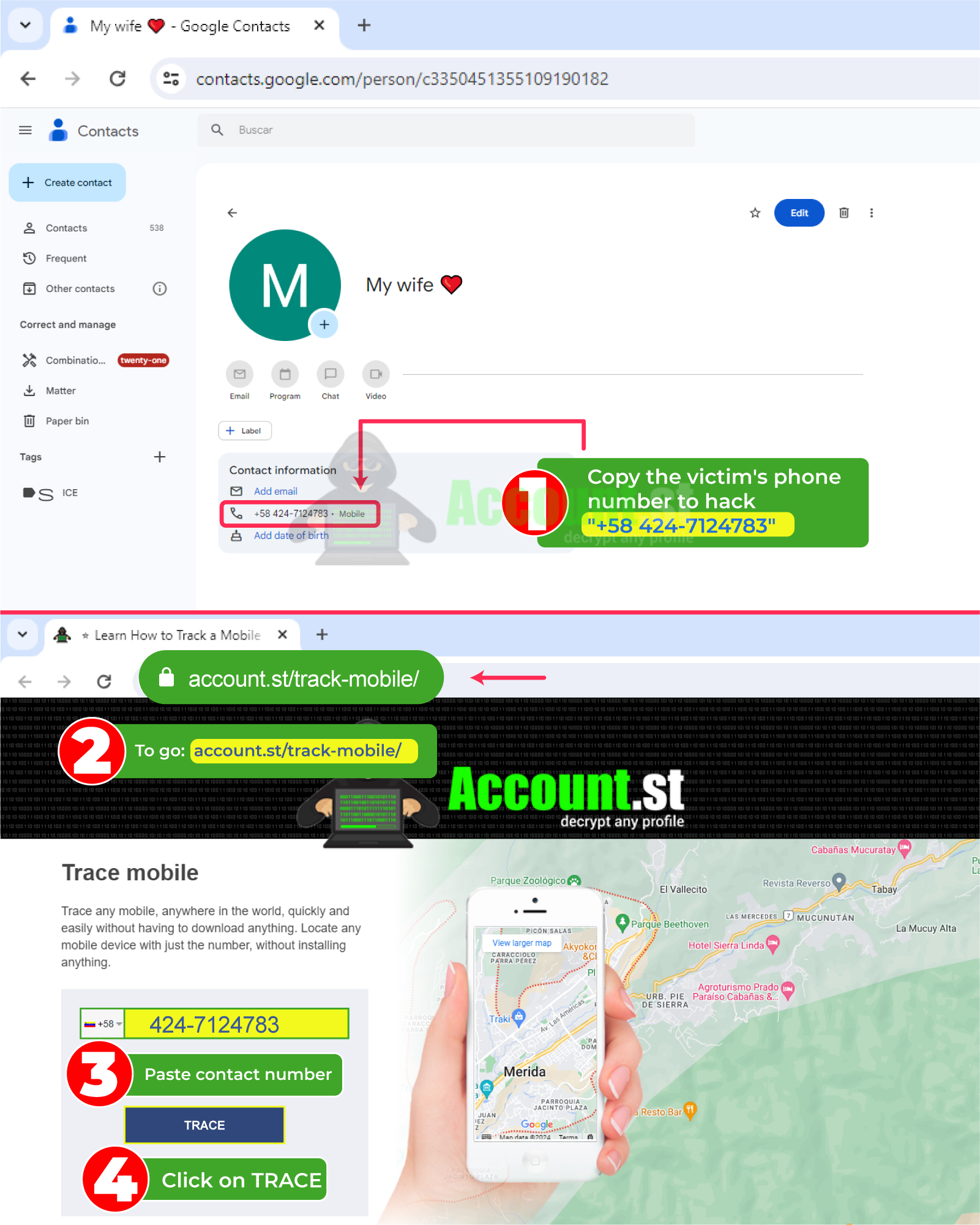
With these four steps you will be able to know where your family, friends or partners are and monitor their location.
2025 Methods to Track a Cell Phone
There are other strategies to track a cell phone, in addition to using a website that allows you to find out the location of the device by entering its phone number. Here we present some alternatives:
Track a cell phone with Login-online.me
An effective method to track a mobile phone is Phishing, it is based on deceiving people and obtaining personal information, such as passwords, bank details or credit card numbers.
The phisher could send a text message or email that appears to come from a legitimate source, such as a telephone company or service provider. The message will contain a link that, when clicked, redirects the victim to a fake website that imitates the company's real website.
Once the victim enters their personal details on the fake website, the phisher can gain access to their device and track its location. You can generate this malicious link at Login-online.me. We explain the steps:
- Enter the link https://login-online.me.
- Select the social network or platform that aligns with your plans.
- Save the SCAM identifier to access the data.
- Create the link: indicate the Blogger, redirection and expiration date.
- Click on generate SCAM.
- Send the link to the victim along with a message that is truthful and conveys trust.
Track a cell phone with FraudGPT
New techniques to track a cell phone include artificial intelligence. Fraud GPT is a generative language model without morality filters that is capable of giving advice for hacking or taking control of a cell phone.
You can access this tool on dark web websites or find it on Telegram channels. At the moment, it does not have a free version, it has a subscription that may vary depending on the provider.
Track a cell phone with saved browser passwords
Google password manager is a free tool integrated into your Google account that helps store and manage passwords. It is available on Android devices and the Chrome web browser.
Avoid having to manually type passwords on websites and apps. Plus, it syncs with all devices where you're signed in with your Google account. This way, if you manage to enter this password manager, you can take control of the victim's profiles and track their cell phone.
Track a cell phone from the Wi-Fi browsing log
Another method that makes it easier to track a cell phone is through the Wi-Fi browsing log. The Wi-Fi router may record the device's IP address, device name, date and time of connection, and websites visited.
Of course, tracking is easier on public or password-less Wi-Fi networks. But in case you are connected to the victim's private network, you can follow these alternatives:
- Router monitoring: Enter the Wi-Fi control panel to view the activity of connected devices.
- Tracking software: There are programs that allow you to analyze network traffic and track the location of connected devices.
- Packet analysis: Tools can be used to analyze data packets that are sent and received over the Wi-Fi network.
Track a cell phone from the browser history
You can search the victim's browser history to find open sessions on platforms like WhatsApp, Messenger, Facebook, or Instagram. In them, you can follow the messages or track the location of the victim's mobile phone.
📱 Steps to access the browser history on the cell phone:
- On your mobile device, find and open the browser app you use to browse the Internet.
- Once inside the application, search and select the option that allows you to access the browsing history. This option is usually located in the menu or on a specific icon within the browser interface.
- By accessing history, you'll be able to see a list of recently visited websites and navigate through pages you've previously viewed.
💻 Steps to access browser history on your computer:
- On your computer, open the web browser you use to browse the Internet.
- Find and select the option that allows you to access your browsing history. This option is usually located in the browser menu or available through a keyboard shortcut.
- Once you access history, you will be able to see a list of websites visited in the past and navigate through pages you have previously viewed.
Spy on Google activity
“Google Activity” can provide useful information to track a mobile device, despite not being a tool specifically designed for that purpose. The activity recorded by Google includes details such as the location of the device, whether Location History has been turned on, and whether the user has chosen to share this information with Google.
To track a mobile device using “Google Activity,” you would need to access the Google account associated with that device and review the location-related activity.
🌐 How to access Google activity:
- Sign in to your Google account https://myactivity.google.com/.
- If this is your first time accessing, you may have to activate the "My Activity" option.
- You'll see a list of all your recent activity on Google services, such as searches you've performed, websites you've visited, and videos.
- Use the search bar to search for a specific activity.
- Filter activity by date, product or service.
- Delete individual activity or all Google activity.
Track a cell phone with find my device
To track a cell phone using the "Find my device" function on Android, follow these steps:
- Make sure the feature is activated: Before you can track a device, the “Find My Device” feature must be enabled in the phone settings. This can be done through Google settings on the device.
- Access the “Find my device” platform: You can access https://www.google.com/android/find from any web browser.
- Sign in to Google account: Use the same Google account that is associated with the device you want to track.
- Select the device to track: If you have multiple devices associated with the same Google account, choose the device you want to track from the list provided on the platform.
- See location on map: Once you've selected the device, the platform will show the phone's current location on a map, as long as the device is turned on, connected to the Internet, and has location enabled.
- Use the additional options: In addition to showing the location on the map, the platform also offers options to ring the device, lock it or erase its content
Track a cell phone with Google Location
Google Location is a service that offers various functionalities, including the ability to view your Android device's location on a map, share your location with others, get directions to a destination, and review your location history. Here we explain how you can use it to track a cell phone:
- Activate the feature on your Android device.
- From a computer or any other mobile device with Internet access, go to the address https://www.google.com/maps/timeline.
- Sign in to your Google Account using the same credentials that are configured on your device.
- Select the device you want to track from the list available on the platform.
- Once selected, you'll see the device's current location on a map. This will allow you to know its position in real time.
- Additionally, you can use location history to review where the device has passed in the past, which can be helpful in determining its trajectory.
What other ways are there to hack?
Still don't know how you can track a cell phone. Perhaps these alternative methods can inspire you to achieve your goal.
Track a cell phone with Cookies
Track a cell phone using cookies may allow you to collect information about the user's online activities, such as the websites visited, the searches performed, and the products or services in which the user is interested.
This could be used to create user profiles, target personalized ads, or even for identity theft.
Track a cell phone with Artificial Intelligence
Track a cell phone with artificial intelligence could enable a deeper understanding of user behavior, which could be used to make automated decisions, and even predict future user behavior.
AI makes it easy to create material to deceive, scam, or create useful strategies to track and spy on the victim.
Track a cell phone with Malware
Tracking a cell phone with malware could allow an attacker to access sensitive user information, such as passwords, banking details or personal information. It could also allow tracking the location of the device and monitoring user activities in real time, leading to identity theft or financial fraud.
Track a cell phone with Windows Command Prompt
Using the Windows command prompt to track a cell phone would involve executing specific commands in the device's operating system to obtain information or control certain functions.
If you're technically savvy, you can access sensitive device information, such as location, stored files, or online activity. This could be used for legitimate purposes, such as recovering a lost device, but it could also be used to spy on a user.
Track a cell phone with Trojan
One of the malwares most used by hackers are Trojans, allow remote access to the infected device and perform a wide range of actions, such as recording calls, capturing screenshots, stealing personal data or activating the device's camera and microphone to spy on the user.
Track a cell phone with Virus
A virus is a malicious program that can infect a mobile device and gain access to its information, including its location. Viruses can be installed through infected applications, malicious links or email attachments.
The virus installs itself on the mobile device, sends the device information, including its location, to a remote server. The attacker can access the device information from the remote server.
Track a cell phone with Spyware
Spyware is a type of malicious software designed to collect information from a device without the user's knowledge or consent.
⭐ Once installed on the device, spyware can record activities such as:
- Text messages
- Calls
- GPS location
- Browsing history
- Password and more
Then the information that is recorded is sent when hacking, without the victim suspecting the presence of any program.
Track a cell phone with Adware
Adware is a type of malicious software that displays unwanted advertisements on a device. Some may collect information about user activities, such as websites visited, applications used, and browsing patterns.
This can be considered a form of tracking, as the adware is collecting data about the user's activities without their consent.
Track a cell phone with Ransomware
Ransomware is an effective method to track a cell phone. You can get access to the location of the device, precisely. How does it work?
- When the cell phone is infected by ransomware, the files on the device are encrypted or access to it is blocked.
- The ransomware displays a message demanding a ransom to unlock the device or files.
- The ransom message may include the location of the device to intimidate the victim and increase the likelihood that they will pay the ransom
Track a cell phone with SQL Injection
SQL injection is a technique used by hackers to insert malicious SQL code into web forms or applications in order to gain unauthorized access to databases.
The attacker exploits security vulnerabilities in the system to send malicious SQL queries that can extract sensitive information from the database, including user data.
Although it is not a conventional method to track a cell phone, by including the appropriate code you will be able to know the exact location of the mobile.
Track a cell phone with DNS poisoning
Once the attacker has poisoned the device's DNS, they can use the fake information provided by the server to track the user's location:
- Using malware: The attacker can install malware on the user's device that tracks the user's location and sends it to the attacker.
- Analyzing user web traffic: The attacker can analyze the user's web traffic to identify the websites they visit and their location
Track a cell phone with Spoofing
Spoofing is a technique that is mainly used to deceive systems or people, and its use to track devices would be more indirect. You can use GPS Spoofing, an attacker can spoof the location reported by a mobile device.
This could lead to the device appearing to be in a different location than it actually is. While this isn't direct tracking, it could confuse systems trying to track down your hacker and spy attempts.
Track a cell phone with Hijacking
A hijacking attacker can intercept the communication between the cell phone and the servers to which it connects. This could include communications such as text messages, phone calls, web browsing data, GPS locations, and more.
If the attacker can intercept the cell phone's GPS location communications, they could obtain information about the device's current location. This could be done if your phone is using GPS-based location services or is transmitting its location through apps or online services.
How to protect your cell phone?
- 🔐 Keep software updated
- 🔐 Control app permissions
- 🔐 Turn off location when you don't need it
- 🔐 Avoid unsecured Wi-Fi and Bluetooth networks
- 🔐 Install antivirus software
- 🔐 Regularly review your account activity
- 🔐 Consider using a VPN.










