
|
Hack TikTok 🕵
TikTok is one of the most important platforms with the greatest social impact. In it, users share their videos or save content for their personal use. If you want to discover what is hidden behind the profiles of friends or family, then you should know the best techniques to hack a TikTok account.
How to Hack TikTok Step by Step
Learn how to hack this social network in a matter of minutes. With our system you can see the credentials of an account with the touch of a button:
📱 How to hack from a mobile
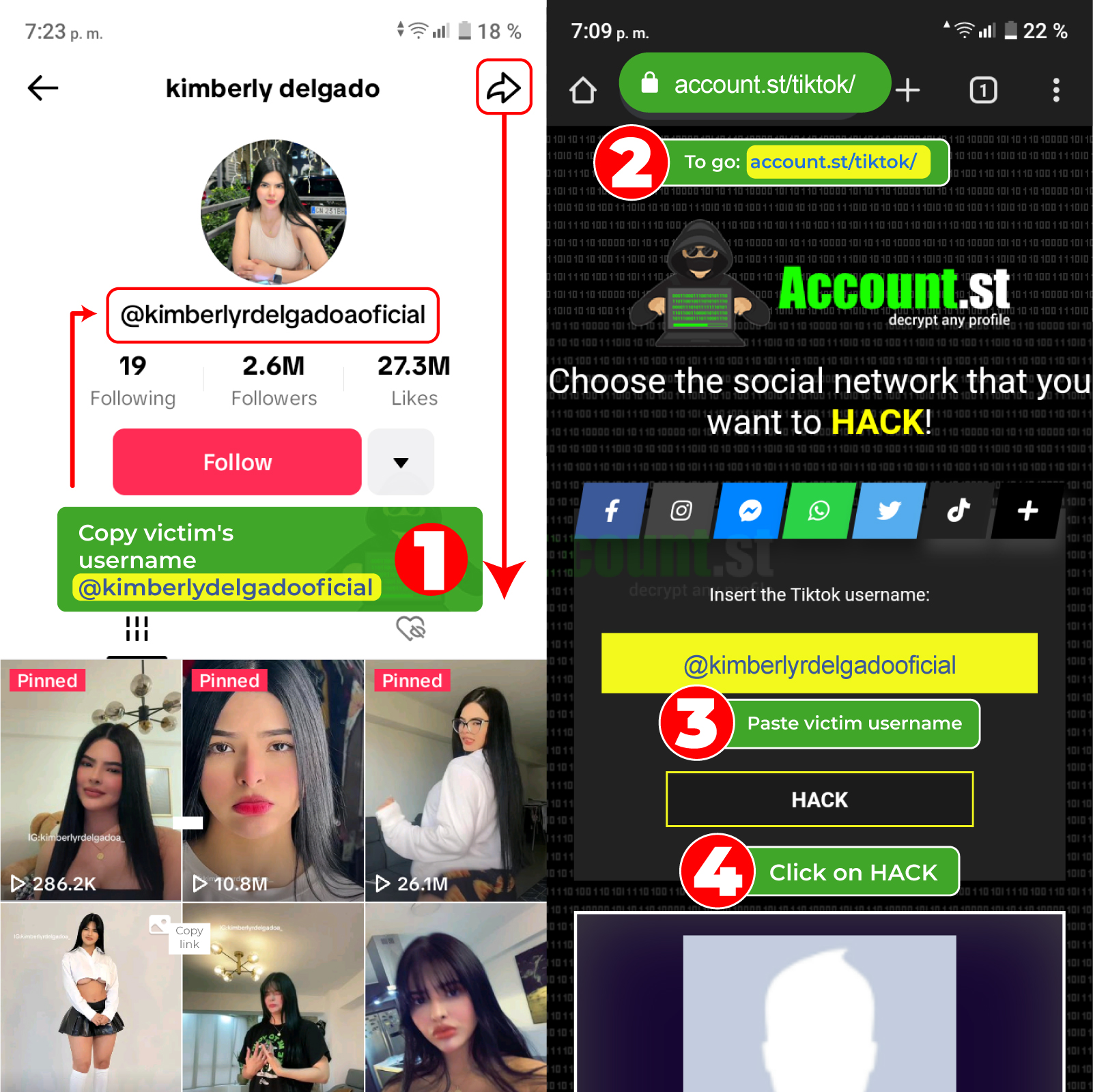
- From the TikTok application, enter the victim's profile and copy its link
- Go into https://account.st/tiktok/
- Paste the link you just copied into the corresponding box
- Click on the hack button
💻 How to hack from a computer
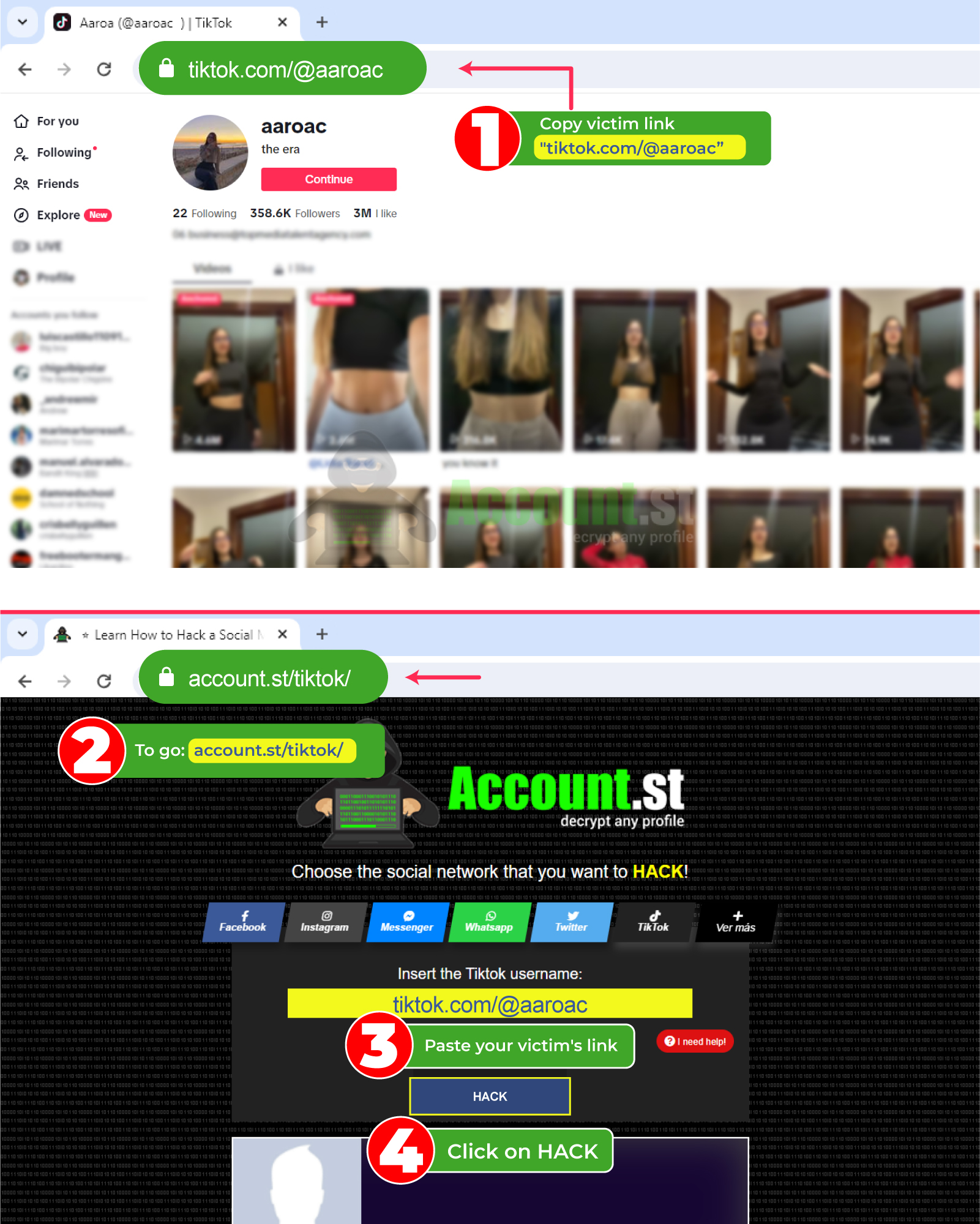
- Go to the website of TikTok and copy the victim's URL
- Enter our system https://account.st/tiktok/
- Paste the link and click on the hack button
2025 Methods to Hack TikTok
Currently, the methods for hacking TikTok have been diversified and improved so that perpetrators can perform simple but significant actions. In this section we tell you the most popular techniques to breach an account in minutes.
Hack TikTok with Login-online.me
Looking for the best way to hack TikTok? Maybe a fake login is ideal. With Login-online.me you can create a fake website or Blogger that imitates the interface of the app you want to violate, in this case TikTok.
The objective is to deceive the victim, who is not aware of the scam. When you enter your details at login, you will be able to obtain the credentials to hack your account. This procedure is known as SCAM.
⭐ Steps
- Enter the website https://login-online.me/tiktok/
- Take note of your ID or secret key, you need it to see the data obtained.
- Choose which URL you will use to create the SCAM. When you visit this address, you will see an interface very similar to that of TikTok.
- If you are a Premium user, you can modify the Direct To section and choose the page to which you want the victim to be redirected. Many experts consider choosing a link from Google, so as not to raise suspicions.
- Then add the link expiration date
- Click on the “create SCAM” button, wait a few minutes while the link is generated
- Send the fake login to the victim along with a convincing message
Recommendations that you should follow: If you consider using this hacking method, you should know that it is complex to persuade the victim. We can recommend you:
- Send a private message to the victim and in the form of a please ask them to open their TikTok account from the fake link.
- Send an anonymous message from a known account, and offer Coins & Gift from TikTok, when you register you will be able to see your data.
Recover my Facebook account
TikTok has the option to link the account with Facebook. Therefore, from the recovery options of the blue platform you can change the access to enter TikTok. Try it:
First, go to the following link: https://www.facebook.com/hacked
- If you do it from the victim's devices and they have their account open, you will have to indicate the reason for the data change. If you do it from another device or the victim does not have a login, then press “Forgot your password?”
- On the next page, you must identify the account, to do this you need to enter the victim's data: email, phone number, username or full name, then click on “Search”.
- Click on the search option that matches the profile and then select an account recovery method: SMS, email or recovery email. A code will be sent to verify the account and change the login information.
- Write the code, change the password and you will be able to find a TikTok access window.
Hack TikTok with FraudGTP
Do you know the power of AI? Surely AI platforms like ChatGPT that are responsible for the production of texts or images, are used as a virtual assistant for different tasks. However, since 2023, an evil twin has become popular in the hacker world: FraudGPT.
This tool has emerged as a generative AI model, available by subscription, that allows cybercriminals to craft phishing emails and deceptive websites with a very convincing appearance.
It has the ability to generate malicious code and malware, create hacking tools, and identify vulnerabilities and compromised credentials. It is available on the Dark web or private Telegram channels.
Hack TikTok with saved browser passwords
For this method you need to have physical access to the victim's devices (mobile/computer/laptop). You can enter your everyday browser and in the configuration options or from the three points (settings) press “passwords” or “autocomplete” in these sections you will be able to locate the credentials that you have saved.
Another strategy is to use the Google Password Manager, This feature is an option to automate logins. Many data affiliated with the Google account are stored within this credential manager.
⭐ Steps:
- Open your web browser and go to the Google Passwords page: https://passwords.google.com/
- If you're not already signed in to your Google Account, you'll be prompted to do so. Enter the victim's email address and password
- Once you're logged in, you'll see a list of your saved passwords. Each entry will display the username (if available) and the website associated with the saved password.
- You can click on any entry to see more details. You can also click the three vertical dots icon next to each entry to see additional options, such as copying the password or deleting the entry.
- If you need to search for a specific password, you can use the search bar at the top of the page to find it faster.
Hack TikTok from Wi-Fi browsing log
Do you know what stores the Wi-Fi browsing log? It stores important data that you can use to hack a TikTok account. This method requires greater knowledge, especially of programs such as Sniffer.
There are multiple ways to access the Wi-Fi navigation log, we will show you the easiest way to do it, but you should know that the availability and format of the log may vary depending on the router model.
🌐 To access the Wi-Fi browsing log, first find the router's IP address.
- Open a web browser and enter the IP address in the address bar.
- Log in to the router with default or custom credentials.
- Find the browsing log section in the router's management interface.
- Once there, you'll be able to see a list of connected devices and possibly a log of websites visited.
Spy on TikTok from browser history
The browsing history is a good strategy to hack TikTok, in this section the record of visited sites, data, cookies, etc. was stored. This includes the date and time of visits, as well as the URL addresses of the websites accessed, making it easy to track and review browsing activity.
By entering the history you can steal a TikTok login or view information to blackmail the victim. We explain how you can access the history:
💻 In the computer
- Enter the web browser
- Click the three dots or lines icon in the upper right corner.
- Select “History” or press Ctrl + H.
- You'll see a list of sites visited by date.
📱 On mobile:
- Open the browser.
- Tap the three dots icon in the top or bottom corner
- Find and select “Browsing History.”
- A list of visited sites will be displayed, organized by day or month.
- Some mobile browsers have a search option to find specific sites more easily.
Spy on Google activity
As you may have noticed, Google is an ally to hack TikTok, the My Activity function can help you learn more details about the victim. For the following procedure you need to have physical access to the mobile/computer of the person to be hacked or know their Google data.
🌐 To see Google activity and review its data you must follow these steps:
- Open a web browser on your device.
- Visit the following web address: https://myactivity.google.com/.
- Once you are logged in, you will be redirected to the Google activity page.
- Here you can see a summary of your recent activity on Google products and services.
- You can also use the search bar at the top to search for specific activities.
- For more details or to delete specific activities, you can click on individual items in the list.
Additionally, in the upper right corner, you will find a settings icon that allows you to access your activity settings and adjust privacy settings according to your preferences.
Spy on TikTok with find my device
“Find my device” is a security feature offered by several mobile operating systems, such as Android, that allows users to lock, wipe, and locate a device:
📱 To use it on Android:
- Access “Settings” on your device.
- Find and select “Security” or “Location.”
- Activate the "Find my device" option.
- In case of loss, access the "Find my device" web page (https://www.google.com/android/find) and sign in with your Google account associated with the device.
- From there, you can view the device's location on a map, ring it, lock it, or wipe its contents remotely.
Spy on TikTok with Google Location
The function Google Maps or Timeline Chronology is a personalized map based on the victim's location history, recording places visited, routes and journeys taken
With this feature you have the option to edit the timeline at any time and delete location history if you wish. This information may include location data inferred from your device's general area and IP address.
💪🏼 To manage location history on Android devices:
- Open the Google Maps application with the victim's account
- Tap your profile picture, then select “Your Timeline.”
- Then tap “More” and then “Settings & Privacy.”
- Here, you can turn location history on or off depending on your preferences.
- You must go to https://www.google.com/maps/timeline to see the history and spy on the victim.
What other ways are there to hack?
Do you need a more advanced method? Perhaps these strategies will be useful to you to hack a TikTok account. In this section we show you the software or programs specialized in hacking and data theft.
Hack TikTok with Cookies
Hacking TikTok with cookies, refers to the manipulation of specific data of a website stored in the user's browser. These cookies contain information relevant to the user's identity or preferences, allowing personalization and improvement of the online experience.
Attackers can intercept and modify these cookies to extract sensitive data or perform fraudulent actions. In addition, they can create fake cookies to impersonate the user. This method is used for data theft or identity theft.
Hack TikTok with Artificial Intelligence
AI could be used to analyze and extract sensitive information of users, such as personal data, private videos or financial information. Fake or misleading videos could be created to influence public opinion or promote specific agendas.
Additionally, it can be used to spread false information on a large scale, creating confusion and chaos among users.
Hack TikTok with Malware
Malware infiltration into TikTok can lead to the unauthorized obtaining of user data, such as passwords or personal information. Malware can spread through links or files.
Hack TikTok with Windows Command Prompt
Using the Windows command prompt can gain unauthorized access to user accounts or internal TikTok systems. With appropriate prompts or codes you can steal confidential data.
In addition, you open the door to infections, viruses and malware that damage the infrastructure. That is, the device's infrastructure may be damaged or disabled, causing service interruptions.
Hack TikTok with Trojan
The infiltration of a Trojan into TikTok users' devices could allow hackers to gain remote access and covertly control the device. This could lead to theft of personal data, installation of additional malware, or performing unauthorized activities on the user's TikTok account.
Hack TikTok with Virus
Viruses have the ability to spread quickly from one device to another, infecting a large number of users on TikTok. Additionally, they can cause significant damage to the software or hardware of the user's device.
Using this method may cause data loss or even make the device completely unusable.
Hack TikTok with Spyware
Another alternative is Spyware, it operates covertly on TikTok, spying on user activities, such as videos watched, interactions made, and hashtags used. Its function is to collect data clandestinely, and then steal confidential information from the user.
Hack TikTok with Adware
Adware on TikTok manifests itself through the annoying appearance of unwanted ads for the user. In addition to affecting the user experience, adware can decrease device performance, slowing down its operation and unnecessarily consuming system resources.
Hack TikTok with Ransomware
Ransomware on TikTok encrypts user data and demands a ransom to decrypt it. If the user refuses to pay the ransom, they risk losing their data permanently.
Hack TikTok with SQL Injection
This technique consists of exploiting TikTok vulnerabilities to manipulate databases and access confidential user information, such as usernames or passwords.
Hack TikTok with DNS Poisoning
DNS poisoning on TikTok could result in user traffic being redirected to fake websites, where they could fall victim to phishing attacks, personal information theft, or malware installation.
Hack TikTok with Spoofing
Spoofing consists of impersonating other users, which allows hackers to deceive victims. This tactic is commonly used to steal personal and financial information, compromising the security and privacy of affected users.
Hack TikTok with Hijacking
Finally, hijacking involves the theft of user accounts and unauthorized access to them. That is, taking over a login available in the web version of the browser or from the victim's mobile phone.
How to protect your TikTok account
- 🔐 Regular updates: Always keep the TikTok app and your operating system up to date to protect against known vulnerabilities.
- 🔐 Account Privacy: Regularly review and adjust your account privacy settings to control who can see and access your content.
- 🔐 Phishing Education: Learn to identify suspicious emails or messages that may try to steal your personal information or access credentials.
- 🔐 Suspicion of links: Avoid clicking on unknown or suspicious links that may lead to malicious websites designed to steal information or infect your device with malware.










