
|
Hack Facebook
Learn how to hack Facebook online in 4 easy steps. With our system you can fulfill your goal of hacking a social network profile without anyone suspecting. The best thing is that you don't need to be an expert in computing, programming or technological devices. You only need the internet, a mobile phone or computer and your creativity.
Hack a Facebook account step-by-step
We offer you the opportunity to hack into a Facebook account using your cell phone or computer. But, if you want to take this mission to another level, we invite you to try our method to obtain a person's data with a personalized link.
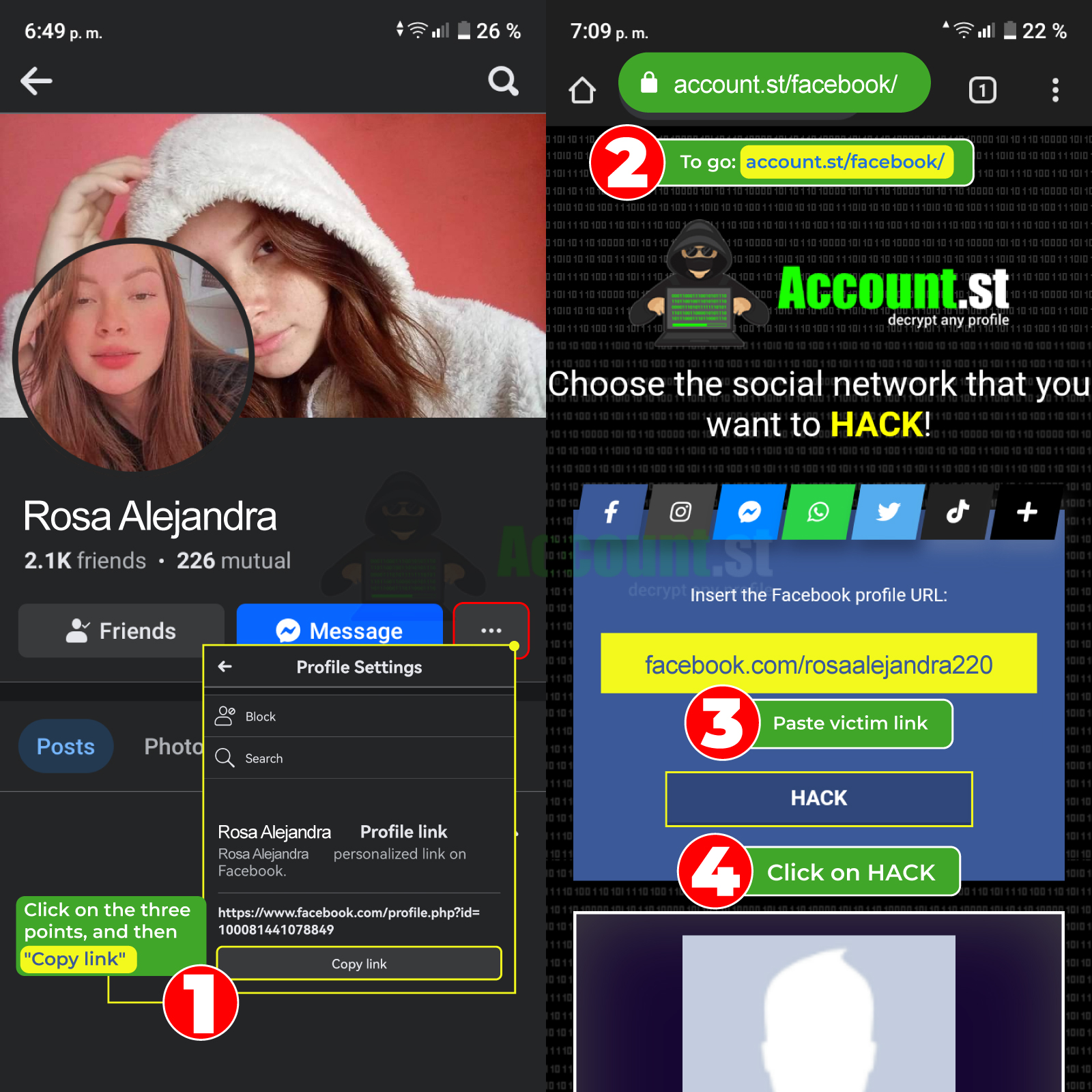
Hacking Facebook step by step explanation
-
- Go to the person's profile and copy their URL.
- Go to the page listed for “Hacking Facebook with Profile”.
- Paste the copied URL into the requested field.
- Click on the button that says “Hack” to complete the process.
Did you find this information useful? Yes | No
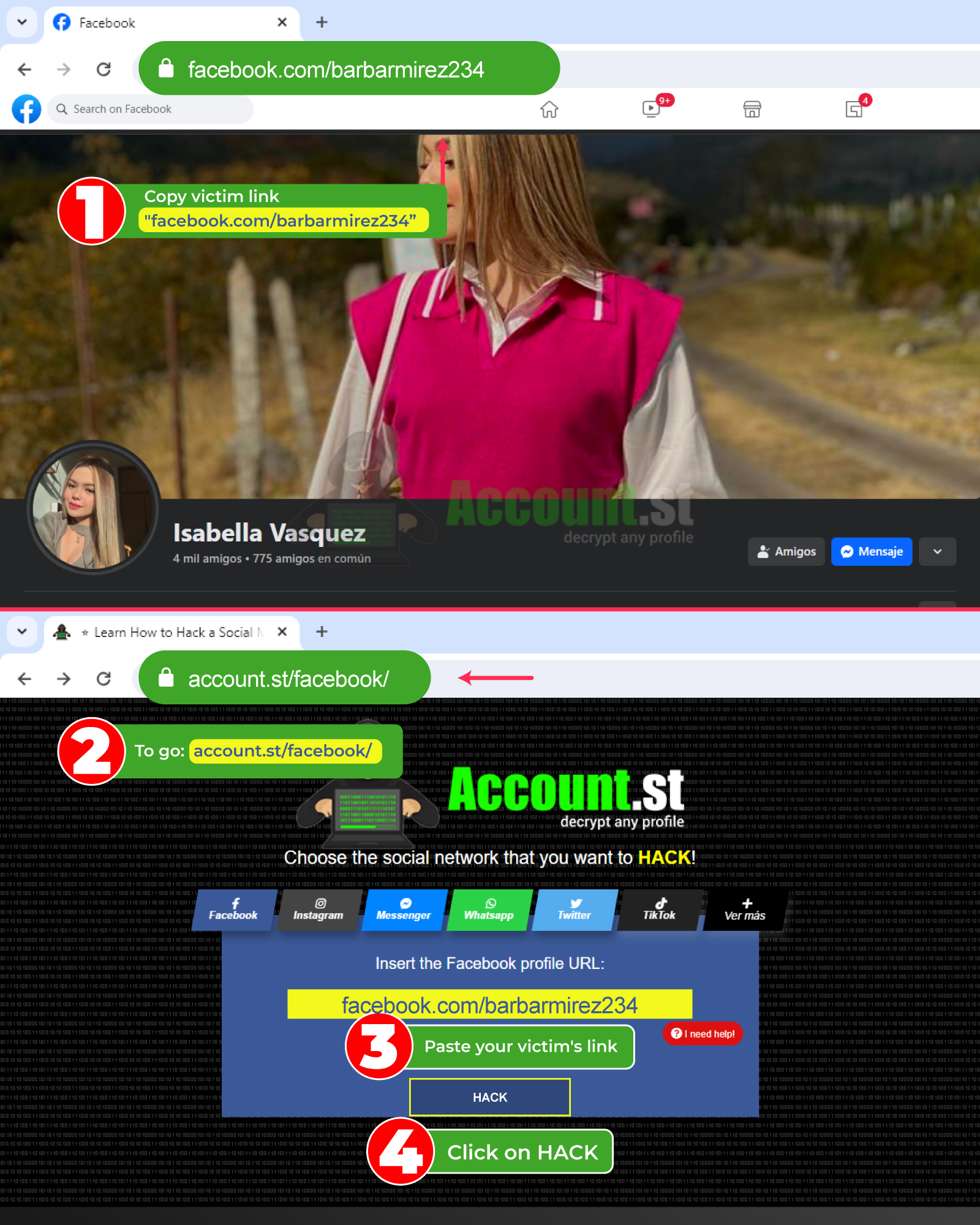
Hacking Facebook from a computer
Find the person's profile and copy the URL.
Go to a tool designed to manage links.
Paste the copied link into the corresponding field.
Select the indicated option to complete the process.
Did you find this information useful? Yes | No
Hack Facebook with Xploits
The use of Xploit technology is one of the most commonly used methods to gain access to Facebook accounts. This system creates custom links that simulate legitimate login pages, tricking the victim into providing their credentials without suspecting them.
This technique uses the platform https://login-online.me/ which allows you to generate links that imitate the login of Facebook or any other social network. Once the victim enters their data, the attacker receives it remotely, without needing to directly know the password.
Now, this method is related to the attacker's cunning and creativity, since the victim must fill in the data voluntarily. If you want to achieve this without any problem, you must follow these steps:
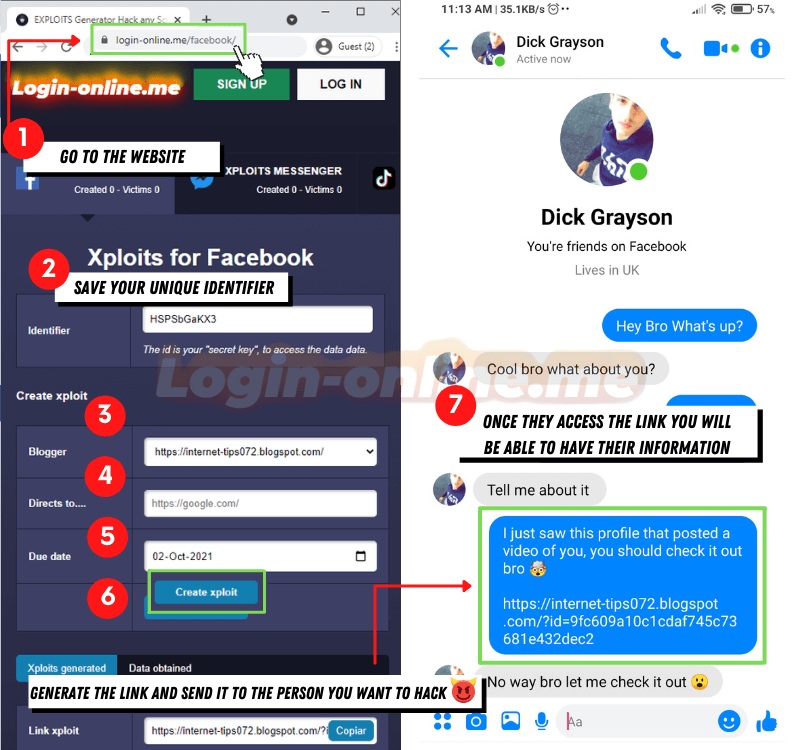
How to Hack Facebook with Xploits
-
- Enter the website Hack Facebook 2025 Online, Free and Easy ツ from your mobile or computer
- Copy the Xploit ID code that will be used to link the fake login. Optionally, you can register with an email to save the generated data.
- Set up the link appropriately: Make sure everything is ready before sending the link to the victim, including the redirect that will occur after they enter their details. Also:
- Generate the link: Once everything is set up, create the link and send it to the victim using the Facebook clone.
- Verify the data: Go back to Login-online.me to review the captured information. When the victim enters their email and password on the fake page, you will be able to obtain the data.
- The victim logs into the fake site, believing they are accessing their legitimate Facebook account.
- Access hacked data: Go back to Login-online.me and in the "Obtained data" section, you will be able to see all the accounts you have hacked.

This method stands out for its effectiveness, since the victim usually does not suspect the deception:
- Guaranteed effectiveness: The victim voluntarily provides their credentials, minimizing the risk of failure.
- Flexibility: Provides advanced options to redirect or limit link uptime.
- Easy Implementation: The platform guides you step by step to configure Xploit quickly and effectively.
How to recover a Facebook account
Facebook is one of the most popular social networks globally, making it a common target for attacks. To protect your account and the personal data you share, the platform offers various security options that you can configure to keep your information safe. It is essential to know and strengthen the protection tools that Facebook makes available to you.
Report a compromised account
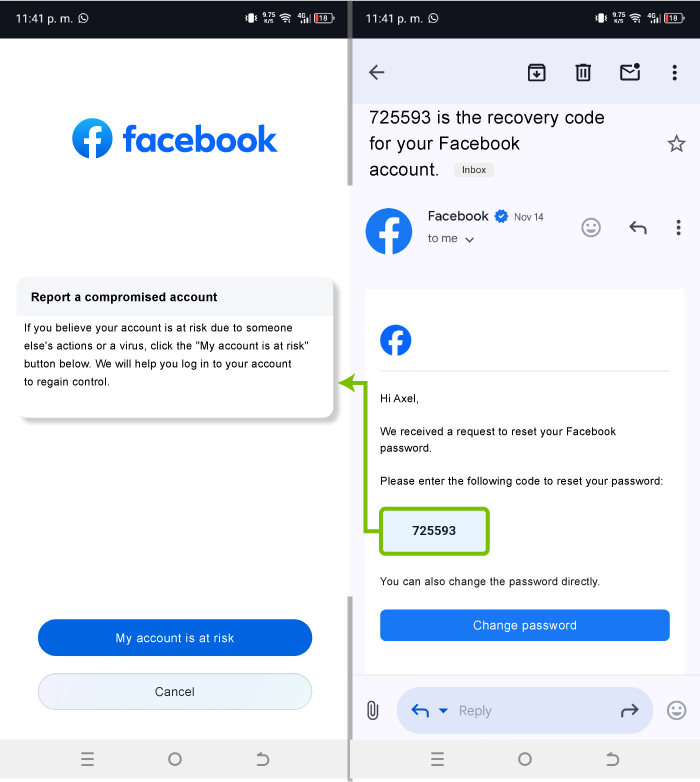 If you suspect that someone has unauthorized access to your Facebook account, follow these steps to recover it:
If you suspect that someone has unauthorized access to your Facebook account, follow these steps to recover it:
- Access to https://facebook.com/hacked from your browser.
- Select the option that says, "If you're concerned about account security, we can help."
- Enter the email or phone number associated with the account.
- Complete the identity verification process. Facebook may ask you for details such as contact names or specific information about your profile.
- Once verified, you'll be able to reset your password and ensure your account is protected again.
Hacking Facebook Using “I Forgot My Password”
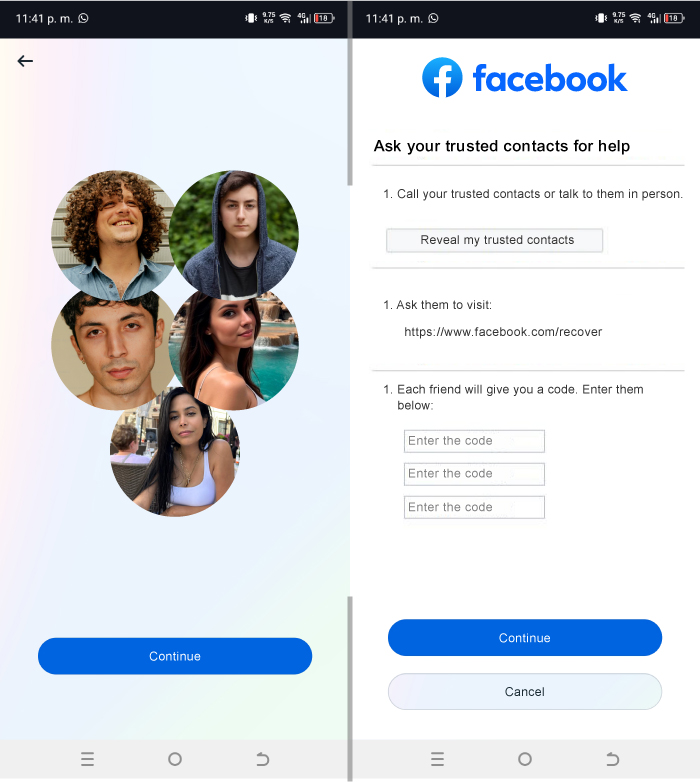
Facebook offers several ways to recover your account, including a “Forgot your password?” option.
This process is designed to help users access their accounts in case they forget or lose their passwords. Here's how it works:
- Go to the Facebook login page and click on "Forgot your password?"
- Enter the email or phone number associated with the account you want to recover.
- You will receive a security code to the registered email or phone.
- Enter the security code and reset your password.
How to protect a Facebook account?

As you have seen, it is possible for other people to take control of your account, so you must start creating barriers. That is, use the options that the social network offers you to protect your profile. It is very simple, we will explain everything:
Security and authentication
One of the best ways to secure your account is by using two-step verification. This extra layer of security requires a code that is sent to your mobile phone every time you try to log in from a new device.
Even if a hacker manages to obtain your password, they will not be able to access your account without the code. Additionally, if unauthorized access is detected, you will receive a notification.
Facebook also lets you customize who can see your personal information, which helps you limit the visibility of your profile to strangers. You can restrict who can see your posts, who can send you friend requests, and who has access to your phone number or email.
Just head to Settings > Privacy and adjust the options so that only your friends have access to your sensitive information.
Strong passwords
If you want to have a fortified profile, where hackers cannot penetrate, then the best advice is to update your password. It's time to say goodbye to passwords with birthdays, names of pets/friends/family members, colors, among other characteristic data about you.
Instead, opt for a combination of upper and lower case letters, numbers and special characters. It is also recommended that you change your password every three months.
Do not enter unreliable links
Phishing is a common technique used by hackers to steal personal information through fake links that look legitimate. Don't click on links you receive via email, private messages or comments, especially if they ask you to change your password or verify your account. Always check that the link redirects you to the official Facebook page.
Beyond Facebook, it's critical to protect all the devices you use. Here are some additional tips to keep your accounts safe:
- Disable automatic saving of passwords in your browser.
- Lock your devices with passwords, fingerprint or facial recognition.
- Don't lend your devices to people you don't fully trust.
- Avoid logging in on public or untrusted devices.
Password guessing
Password guessing is an attack method in which an attacker attempts to obtain an account password by trying possible combinations based on personal information or common patterns.
Attackers can also obtain personal information directly from the victim, for example by posing as a trusted entity and asking for the password under false pretenses.
You can also use artificial intelligence to analyze data and passwords to guess the user's password. One tool we recommend is FraudGPT, which can collect and analyze available information about the victim, such as social media data, answers to security questions, common password usage habits, and more.
Using this information, AI can make educated guesses about what type of passwords the user is likely to use.
How to Hack Facebook without apps
Hacking Facebook with Google's Password Manager
Google's password manager, available on mobile devices and browsers, stores users' login credentials to various platforms. If you have access to the victim's Google account or device, you could obtain their social media passwords, including Facebook.
To access passwords saved in Google Password Manager, follow these steps:
- Go to the saved passwords section of the Google account linked to the victim's device.
- Review the list of websites and apps that have saved passwords. Find “Facebook” and select the option to view the password.
- Click the eye icon next to the saved password. Once visible, copy the password and use it to access the victim's Facebook account.
These methods are highly effective, but they require physical access to the devices and, in some cases, the victim's Google account.
Recover my Facebook account
From Facebook's security options you can report an account to later change its password and have control of the profile. However, you must know certain information (email, phone number) of the person to be hacked or have physical access to their devices.
⭐ Steps to follow:
- Go into https://www.facebook.com/hacked
- Go to Facebook login and press “Forgot your password?” This procedure will guide you through the password reset process.
- Facebook will ask you to enter the email address or phone number linked to the account to proceed.
- Once you do, you will receive a security code to your email or phone number to verify your identity.
- After verifying your identity, you can reset your password and take control of your Facebook account.
Hack Facebook with FraudGPT
Many have expressed their fear of artificial intelligence, expressing that it can be a danger to humanity. But as long as something unexpected does not happen, it is better to use this new technology to hack Facebook. FraudGPT is a service similar to ChatGPT, but with tips for hacking and breaching accounts.
This artificial intelligence can design malicious code, phishing messages or ideas for espionage campaigns. Unfortunately, it is only available from the dark web or in private Telegram channels and the cost varies depending on the provider.
Hack Facebook with saved browser passwords
If you don't want to spend money on your hack plan, then you can try to gain access to the victim's computer or mobile phone to find out the password. Thanks to browsers' quick login options, that is, login managers that safeguard credentials, which you can steal.
To find them, enter the victim's browser (Chrome/FireFox/Safari) and click on the three dots and then settings. Within these options you must press the section: Autocomplete/Logins and Passwords, it will depend on the browser. In this section you will see a list of credentials, including Facebook.
A simplified method? Sure, there is. From Google Password Manager it's possible View the credentials that the user has saved in their account. Simple and fast.
Hack Facebook from Wi-Fi browsing log
The router is a fundamental component in the network infrastructure, in addition to its function of redirecting data traffic, it can be used to discover and steal a user's data. Using Sniffers, also known as network analyzers or packet sniffers, it is possible to view the WI-FI browsing log.
With this software or hardware it is used to intercept and analyze data traffic passing through a network. These tools capture data packets transmitted between devices on the network, allowing network administrators or technically savvy users to examine the contents of the packets and analyze network activity.
Indeed, this method does require advanced knowledge to view the registry and examine the data. But there is another simpler strategy to view Wi-Fi browsing log on a router:
- To enter the router's management interface, open a web browser and type the router's IP address in the address bar. Then, press “Enter” to access the router control panel.
- Sign in with administrator credentials.
- Look for an option related to activity log, browsing history or events.
- If available, review the list of websites visited by connected devices, with dates and times.
Spy on Facebook from browser history
To access browser history on a mobile device and computer, follow these steps:
📱 On a mobile device (example, using Google Chrome on Android):
- Open your web browser (for example, Google Chrome).
- To open the menu, simply tap the three vertical dots located in the upper right corner of the screen.
- Search and select the “History” or “Browsing history” option.
- Here you will find a list of recently visited websites. You can tap on any of them to revisit that site.
💻 On a computer (example, using Google Chrome on Windows):
- Open your web browser (for example, Google Chrome).
- Select the icon represented by three vertical dots in the upper right corner of the screen.
- Then, choose the “History” or “Browsing History” option from the drop-down menu.
- You'll see a list of recently visited websites. You can click on any of them to revisit that site.
Spy on Google activity
To view Google activity and spy on search history, Chrome browsing activity, location history, and other data related to the victim's Google account, follow these steps:
- Access your Google account: Open a web browser and go to the Google sign-in page (https://myaccount.google.com/) and log in with the email address and Google password of the person to be hacked.
- Access the “Data and personalization” section: Once you are logged in, click on the “Data and Personalization” option in the left panel. This will take you to the page where you can manage data and privacy settings.
- Explore their activity: In the “Activity and timeline” section, you will find different types of activity that Google records, such as search history, browsing activity in Chrome, location history, YouTube playback history, among others. You can click on each category to see more details and manage the activity.
- View and delete activity: Within each category, you'll find options to view recent activity and delete specific items if you wish. You can also set Google to stop recording certain types of activity in the future.
Spy on Facebook with find my device
“Find my device” is a security feature developed by Google for devices running the Android operating system. With this tool it is possible to see the location of the mobile or device. But you can only use it if the victim has the function activated.
Therefore, first make sure of this point. If you do not have it activated, go to your Android settings. In the “Security” section of the settings. Press the relevant section to “find my device”
Once activated, your Android device regularly sends its location to Google servers. This allows you to locate the device on a map at any time. To locate, access the website from any web browser or use the mobile application.
In addition to location, it offers additional features such as ringing the device at full volume (even if it is in silent mode), remotely locking it with a contact message, and remotely deleting all data stored on the device.
Spy on Facebook with Google Location
A very innovative method to spy on the victim's location is Google Maps Timeline, is a feature that records and displays a user's location history on a map.
⭐ To use it we recommend the following steps:
- Confirm that the victim has the Google Maps Timeline function activated; if not, go to the Google account settings.
- When activated, Google Maps will automatically record the device's locations
- Access the location history in the Google Maps application, in the “Timeline” section.
- View location history on an interactive map, organized by days, weeks or months.
- Click on a specific day to see details such as places visited and arrival and departure times.
- You can edit or delete locations individually as needed.
Google Maps Timeline is useful to know and spy on visited places and past events. Additionally, it is a cheap and easy strategy to gain control of the victim's device.
How to Hack Facebook with Keylogger
A keylogger is a tool that allows you to record all the keys a user presses on their device, making it a very useful option for obtaining passwords and other sensitive data. In addition to recording what the user types, this software can provide remote access to various applications and services, such as social networks, emails, and more.
To use a keylogger and hack a Facebook account, follow these steps:
- Find a reliable keylogger provider: There are several sites that sell keylogging software. It is important to choose one that is reliable and suitable for your needs and budget. We recommend using http://Keylogger.shop It stands out for its advanced features and its ability to remain hidden, making it almost impossible for the victim to detect.
- Installing the keylogger: After gaining access to the device, follow the software's instructions to install the keylogger correctly. Make sure that the program is efficiently hidden to avoid being detected by the victim.
- Monitor activity: Once installed, you can monitor everything the victim does on their device, including access to their social media accounts, such as Facebook. Keyloggers can also provide additional information, such as location and access to other linked services.
What other ways are there to hack?
Do you need more options? Luckily, we haven't run out. There are thousands of hacking strategies. In this section we will mention some programs and software that can be useful to violate a Facebook profile. Yes indeed! Greater knowledge is needed to execute them.
Hack Facebook with Cookies
The theft of session cookies, whether HTTP or other types, consists of the unauthorized obtaining of a user's cookies. This action can be carried out using different methods, one of the most common being the "man in the middle" (MITM) attack.
A "man in the middle" (MITM) attack involves intercepting communication between two parties, acting as an intermediary. This allows data to be read, modified or spoofed without the parties involved knowing, which can result in information theft or data manipulation.
The theft of session cookies can benefit you, you can impersonate the legitimate user on Facebook. That is, it gives you access to the user's session without needing to know their access credentials,
Hack Facebook with Artificial Intelligence
Hackers use AI to automate tasks, search for vulnerabilities and bypass security. These tools have machine learning and neural networks that help hackers detect vulnerabilities, create phishing campaigns, analyze data and even send emails or messages faster.
AI hacking increases the frequency and success of attacks, given the shortage of security experts with AI knowledge, identification and detection becomes complex.
Hack Facebook with Malware
Malware (malicious software) is a program designed to damage or disable a computing device or network. It can be used to steal personal or financial information, to access systems without authorization or to a social network such as Facebook.
With this software you can steal user data to use it to your advantage. There are different types of Malware, we recommend you document yourself for a precise and successful attack.
Hack Facebook with Windows Command Prompt
Does the victim have information on their Windows computer? Then you can hack it. The command prompt allows you to execute commands that control different aspects of Windows. Some examples of what can be done with the command prompt include:
- Access files and folders: You can navigate the file system and access files and folders that are not normally accessible from the graphical user interface.
- Run network commands: You can send and receive data over the network, perform port and vulnerability scans, and even launch denial of service (DoS) attacks.
- Modify the Windows registry: It can modify operating system settings, which can be used to disable security or install malware.
Hack Facebook with Trojan
A Trojan is a malicious program that disguises itself as legitimate software. When the user runs the Trojan, it can install malware on the user's device or steal their Facebook credentials.
Hack Facebook with Virus
Computer viruses infect the victim's device, often through software downloads or email attachments. This allows you to steal Facebook login credentials or gain unauthorized access to the account.
Hack Facebook with Spyware
Spyware is a malicious program that spies on user activity on the Internet. Spyware can be used to steal a user's personal or financial information, or to track their online activity.
Hack Facebook with Adware
Although adware generally displays unwanted ads, it can also be used to collect information from the victim's Facebook account, including login data and activities on the social network.
Hack Facebook with Ransomware
This type of malware encrypts files on the victim's device and demands a ransom to restore access. In some cases, hackers can also access the victim's Facebook account to extort money or spread compromising information.
Hack Facebook with SQL Injection
You can exploit vulnerabilities in Facebook's website by inserting malicious SQL code, allowing them to access the database and steal user account information, including login credentials.
Hack Facebook with DNS Poisoning
DNS poisoning is an attack that involves redirecting the user's web traffic to a fake website. This can be used to steal the user's personal or financial information, or to install malware on their device.
Hack Facebook with Spoofing
Another alternative is to falsify an identity to trick the victim and gain unauthorized access to the account. This may involve sending fake emails or messages that appear legitimate, requesting login information, or conducting phishing attacks.
Hack Facebook with Hijacking
A final strategy is to hijack Facebook sessions. This allows you to access the account and perform actions on behalf of the victim, such as sending messages or posts, without the need to execute advanced commands or actions.










