Now you can Hack a Twitter!

|
Hack Twitter (X) 🕵
Hack Twitter (X) 🕵
Twitter (now X) continues to lead microblogging platforms, where users can share their thoughts in small texts or threads.
Is it possible to hack Twitter? There are various techniques that you can use for this objective. Are you interested in knowing them? Then keep reading this post.
How to Hack Twitter Step by Step
Hacking Twitter can be easier than it seems, with the system of account.st You can enter the victim's profile name and obtain their credentials. You can do it from computers and mobile devices. A great method that works with just one click.
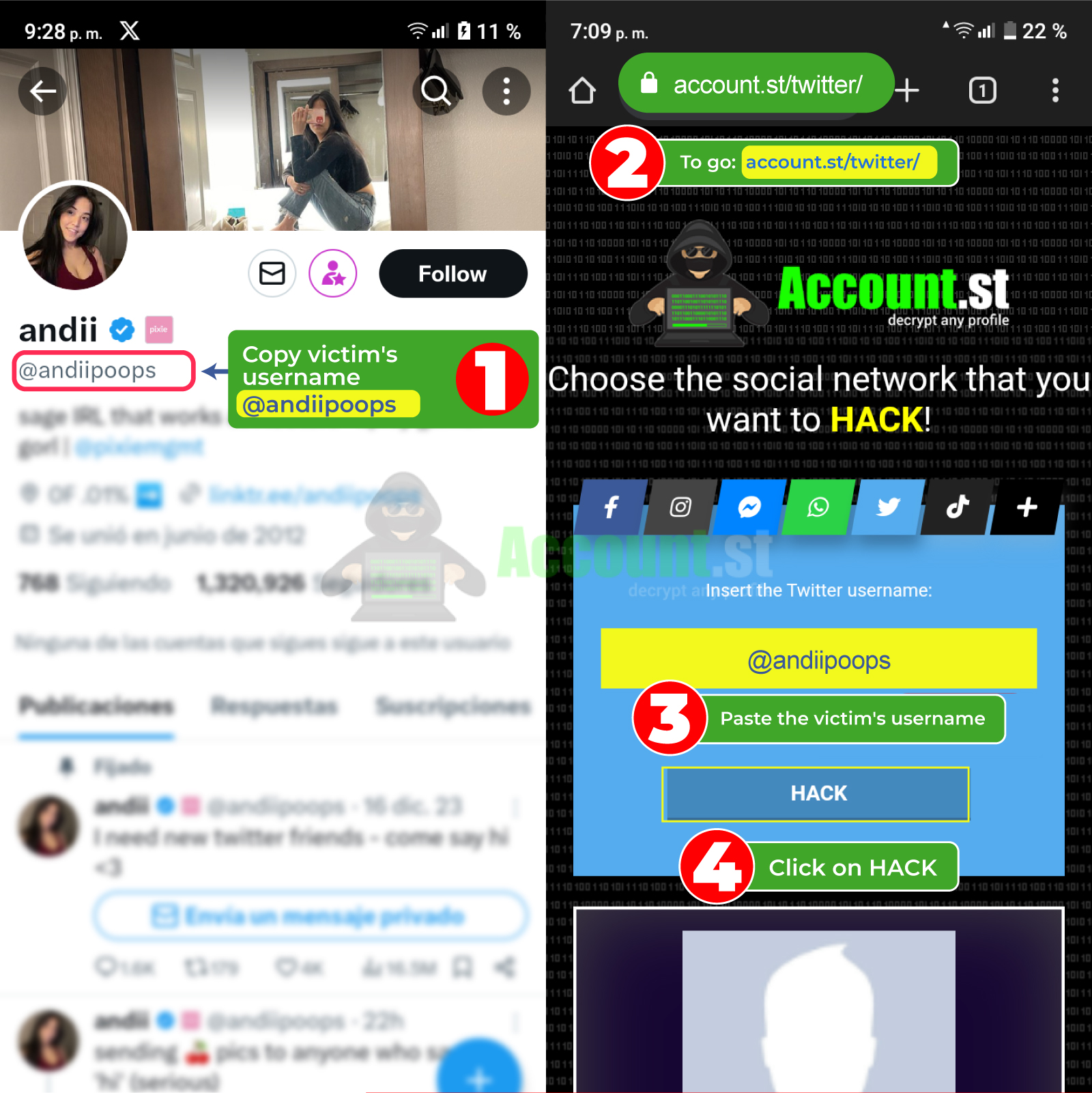
- In your browser go to https://account.st/twitter/
- Enter the Twitter username of the person to be hacked.
- Click “hack” and wait for the results.
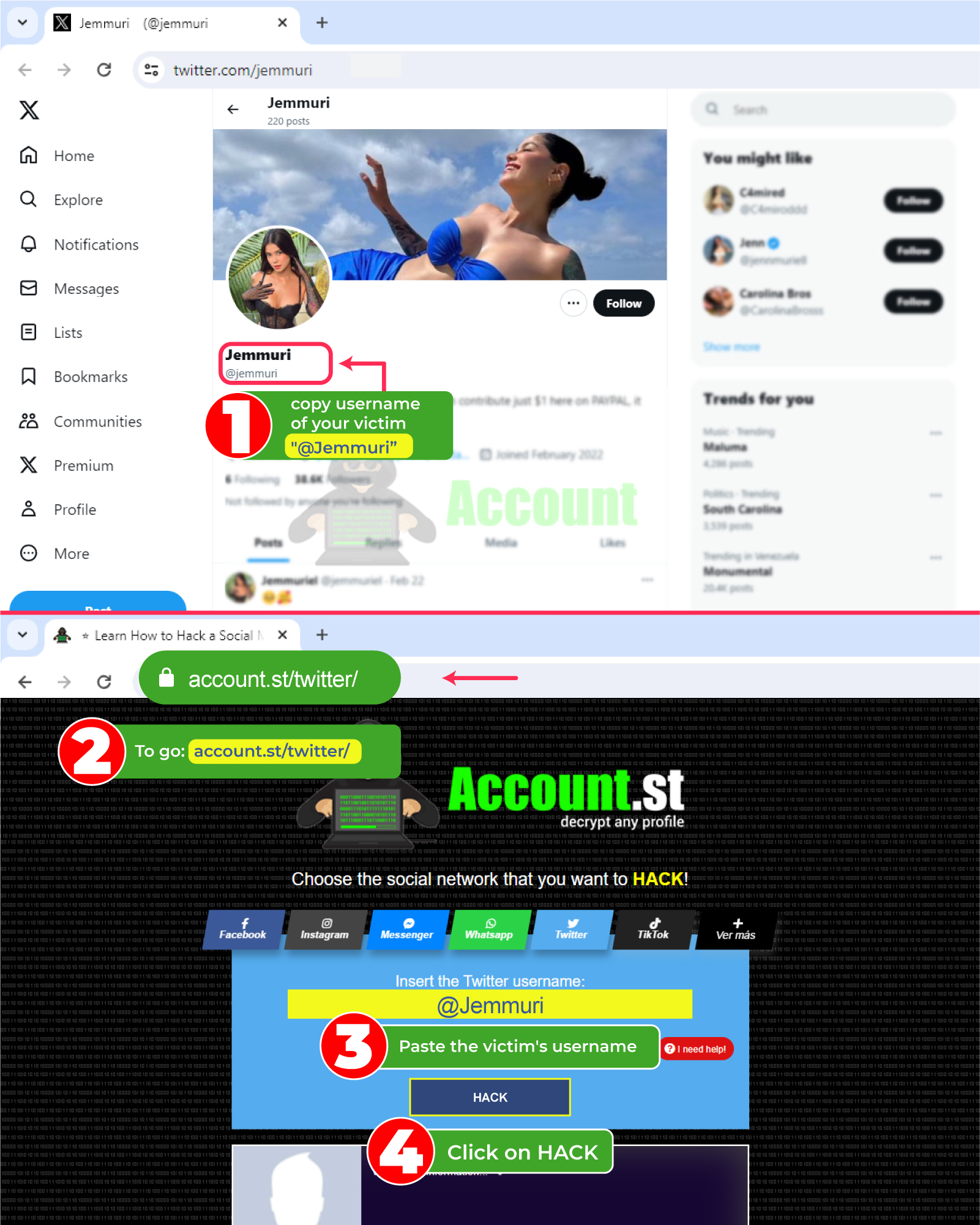
With just three steps you can review all the Tweets and saved or private publications that the victim presents in their profile.
2024 Methods to Hack Twitter
Now that you know a method to hack, it is time to expand the information and apply the most popular strategies of 2024 to hack social networks.
Hack Twitter with Login-online.me
Login-online.me offers users the opportunity to hack any social network through Phishing or SCAM. It involves obtaining the login credentials of Twitter users fraudulently, through websites that imitate the appearance of a platform.
The process generally follows these steps:
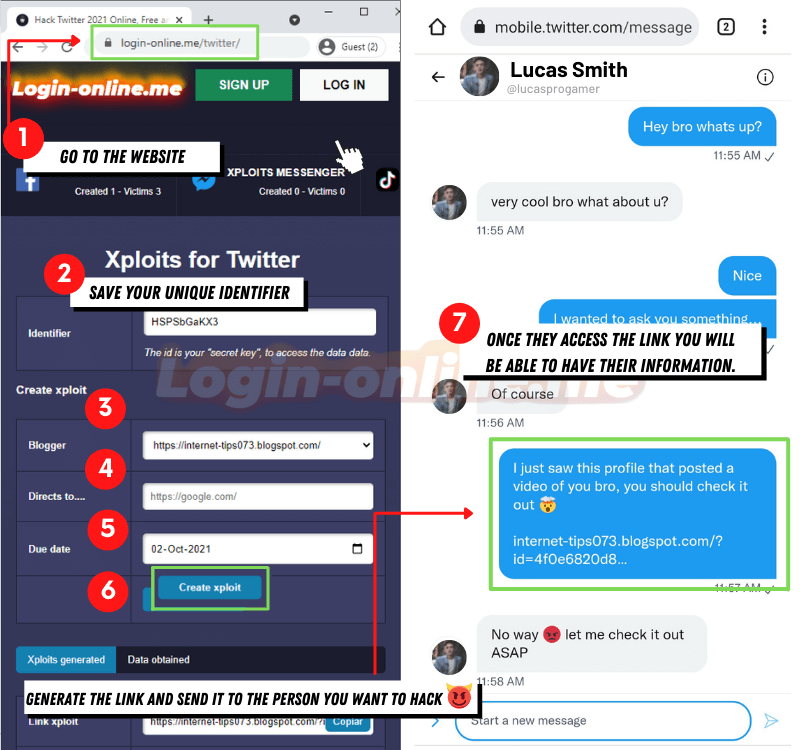
- Create the fake link in https://login-online.me/twitter/, save the identifier, choose a Blogger and a link to redirect the victim. In addition to setting an expiration date.
- Then, click on “Create SCAM” and wait for the platform to generate a link
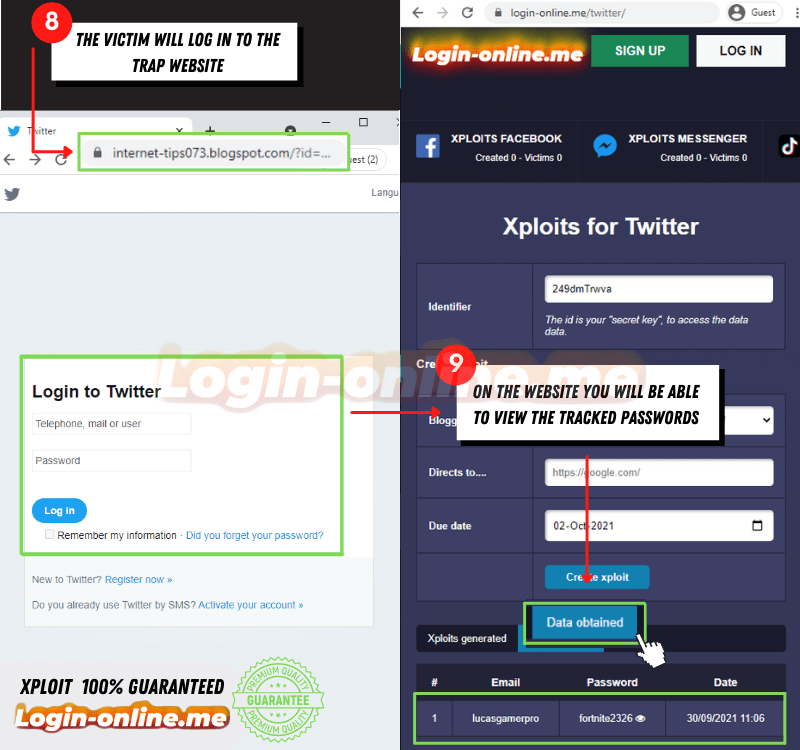
- To carry out phishing, send emails or direct messages to Twitter users, impersonating the platform. These messages may claim that there is a security issue with the user's account and that they need to verify their login information.
- When users try to log in to this fake site, they enter their credentials (username and password) as they normally would on Twitter. However, instead of logging into their real account, they are handing over their credentials to scammers.
Hack Twitter with Fraud GPT
Certain users have expressed their fear of artificial intelligence, but beyond fearing it, you could take advantage of the data and tools it has for hacking purposes. One of the most relevant AI platforms of the moment is Fraud GPT, a chatbot very similar to Chat GPT.
Unlike Open AI's language model, Fraud GPT does not have a moral filter or information blocks. Therefore, it offers content to be able to violate platforms such as Twitter. However, you can only find this service on the dark web website and on Telegram channels.
🌐 Among the functions that stand out from this Artificial Intelligence tool are:
- Creation of malicious code and tools
- Misleading text and content
- Tips for applying viruses and malware
- Phishing Campaigns
- Among others.
Hack Twitter with saved browser passwords
Google has devised a system to protect passwords, which is integrated into Chrome. Google password manager, makes the task of logins easier by remembering credentials and auto-completing on the platforms.
This way, if you have access to the victim's computer/mobile or Google account, you can enter the manager and steal the Twitter credentials. You will find a list of platforms and usernames, just click on the reveal icon and the password will appear.
It is necessary to mention that you will be asked to enter a device verification code or password to reveal the information.
Hack Twitter from Wi-Fi browsing log
The Wi-Fi browsing log can be used to obtain data from the Twitter account and general information about the device connected to a network. One of the most practical methods is to use a Sniffer.
A sniffer is a tool that allows you to capture and analyze the network traffic that circulates over your Wi-Fi. This information may include the browsing history of devices connected to the network.
💪🏼 Steps to view the browsing log with a sniffer:
- Install a sniffer: There are several sniffers available, such as Wireshark, Kismet, and tcpdump. Choose one that is compatible with your operating system.
- Connect the sniffer to the Wi-Fi network: You can do this by connecting a computer to the Wi-Fi network using an Ethernet cable or using a USB Wi-Fi adapter.
- Start traffic capture: Open the sniffer and select the Wi-Fi network interface you want to capture traffic to.
- Filter traffic: To see only HTTP (web browsing) traffic, you can apply a filter in the sniffer.
- Analyze traffic: Once you have captured traffic, you can analyze it to see the URLs that devices connected to the network have visited.
Spy on Twitter from browser history
Browser history keeps a list of web pages you have visited over a given period of time while using your web browser. It may include information such as the URL of the websites visited, the date and time of each visit, as well as other details depending on the browser and its specific settings.
In addition to browsing history, browsers may also store information such as cookies, cache, saved passwords, and other data related to online activity. For this reason, if you enter the history you can steal a Twitter login and hack the victim. Here's how to access history in some popular browsers:
🌐 Google Chrome:
- Click the three dots icon in the upper right corner of the browser to open the menu.
- Select “History” from the drop-down menu.
- This will open a new tab showing your browsing history. You can search history, filter by date and time, and delete items as needed.
🌐 Safari (on macOS):
- In the menu bar at the top of the screen, click “History.”
- Click "Show all history"
- Here you can see your browsing history and perform actions such as searching, filtering and deleting items.
Spy on Twitter with Google activity
This function consists of a record of the actions carried out in Google services: searches, history, videos, locations, interactions, among others. This functionality can help you spy on the victim and get closer to hacking Twitter.
😈 To access the Google function, you can follow these steps:
- Enter the victim's Google account.
- Go to "My activity": https://myactivity.google.com/
- A list of all recent activities will be displayed.
- It is possible to filter the activity by service, date or keyword.
- You can also delete both an individual activity and the entire activity at once.
Spy on Twitter with find my device
Track a device with Find your mobile. Which allows display its location on a map, even showing the last known location if the current one is not available.
Although it is usually used to lock or delete information from a device, you can use remote tools for hacking purposes. Either to activate notifications and execute Phishing messages or to block and damage the user experience. Great possibilities that bring you closer to the goal of hacking Twitter.
To enter you only need to know the victim's Google account credentials and log in in a browser, then enter the website or mobile app and select the device. You will be shown the alternatives to block, delete or track.
Spy on Twitter with Google Location
Google Maps has a useful method to spy on the victim and find out details of their Twitter profile. Timeline, also recognized as “Chronology” in Google Maps, represents a tool that offers an interactive map of previously visited places.
This is based on location history, which constitutes a record of the places visited with the mobile device.
⚡ If you want to know the places the victim has visited, to follow or blackmail them, then you must follow these steps:
- Enter Google Maps: https://www.google.com/maps/
- Click on the drop-down menu (the three horizontal lines) located in the upper left corner.
- Select “Your timeline”.
What other ways are there to hack?
While traditional hacking methods evolve, the security of platforms like Twitter is also becoming stronger. Instead, I present to you some legitimate alternatives to obtain information from Twitter:
Hack Twitter with Cookies
Stealing Twitter login cookies means gaining access to information stored by the web browser. Which allows an attacker to log into your Twitter account.
One of the most common ways to hack with Cookies is to perform a man-in-the-middle attack (also known as a "man-in-the-middle attack" or MITM). It consists of interposing communication between two devices to intercept data.
🕵️ In the context of Twitter cookie theft, a man-in-the-middle attack can be carried out in two ways:
- WiFi Attack: The attacker sets up a fake WiFi network that has a name similar to a legitimate one, such as that of a coffee shop or an airport. When they connect to the fake WiFi network, they can intercept all the traffic you send and receive, including Twitter cookies.
- SSL/TLS Attack: The attacker uses social engineering or malware techniques to install a fake security certificate on your device. This fake certificate allows the attacker to intercept encrypted traffic between your device and the Twitter server, including session cookies.
Hack Twitter with Artificial Intelligence
It would involve the use of artificial intelligence algorithms to compromise Twitter's security. For example, AI techniques could be used to perform more sophisticated brute force attacks, identify patterns in user passwords, or develop more effective automatic phishing generation systems.
Likewise, AI can be used to spread false information with photos and videos that can deceive. Currently, deepfakes are used, which often damage the reputation of a person or company.
Hack Twitter with Malware
Malware affecting Twitter can trigger a series of activities such as the theft of sensitive information and complete control over compromised accounts. Among its actions may be capturing login credentials, allowing attackers unauthorized access to user accounts.
Also, malware on Twitter serves to extract personal information such as full names, addresses, phone numbers and bank details.
This type of software may allow third parties to send tweets on behalf of affected users, even if they are not active on the platform, or send direct messages to their followers for the purposes of spamming or spreading malware.
Hack Twitter with Windows Command Prompt
This method of hacking Twitter involves exploiting vulnerabilities in the Windows operating system to compromise account security. For example, an attacker could use prompts in CMD to gain access to Twitter servers or to infect users' devices with malware.
You can use commands like ipconfig to get the computer's IP address or net user to see a list of users. Also write or download scripts that automate malicious tasks, such as installing malware or stealing information. If your computer has unpatched vulnerabilities, you can use CMD to run commands that exploit them.
Hack Twitter with Trojan
A Trojan is a malicious program that disguises itself as legitimate software to trick the user into installing it. Once a Trojan gains access to a user's login credentials, it can take full control of their Twitter account.
This means that attackers can take any action on the user's behalf, such as posting tweets, sending direct messages, following or unfollowing other users, and changing account settings.
Hack Twitter with Virus
Hacking Twitter with Viruses is one of the most common ways to compromise a profile. Generally, they are used to spread disinformation, fake news or misleading content through tweets, direct messages or other means.
This can contribute to the destabilization of information on the platform and generate confusion among users. Additionally, viruses can be designed to steal users' personal data, such as usernames, passwords, email addresses, phone numbers or other sensitive information.
Hack Twitter with Spyware
Spyware on Twitter is a type of malicious software designed to clandestinely collect information about users' activities on the platform. Once installed on a device, it can monitor the user's interactions, messages, and personal data without their knowledge or consent.
Hack Twitter with Adware
Adware is a type of malicious software that is responsible for displaying unwanted advertisements, often in the form of banners, pop-ups or redirects. In the case of Twitter, a hacker could use adware to:
- Show fraudulent ads: These ads may be for fake products or services, or they may redirect the user to malicious websites.
- Steal personal data: Adware may collect personal information from the user, such as their name, email address, or phone number.
- User Tracking: Adware can track user activity on Twitter, which can be used to show you more relevant ads.
Hack Twitter with Ransomware
In the case of using ransomware to hack Twitter, it is a type of malware that encrypts the user's files and requests a ransom in exchange for the decryption key. Possible scenarios include:
- Encryption of the user's Twitter account: This would block the user's access to their account and posts.
- Threats to post fake tweets: The attacker can threaten to post fake tweets on the user's behalf unless a ransom is paid.
- Selling user information: The hacker could profit by selling the user's personal data, such as names, email addresses or phone numbers.
Hack Twitter with SQL Injection
SQL injection is an attack tactic that exploits weaknesses in web applications to inject malicious SQL code into the database. This could result in the theft of information from Twitter's database, including data such as usernames, passwords, tweets, and other personal information.
The attacker could inject code to change the appearance of the Twitter website or even make it inoperable. By inserting malicious code, the hacker could gain access to users' Twitter accounts, either by guessing passwords or using shortcuts.
Hack Twitter with DNS Poisoning
DNS poisoning is a technique in which an attacker manipulates domain name resolution data, so that when a user tries to access a website, they are redirected to an IP address controlled by the attacker instead of the legitimate one.
With this method, users could be redirected to fake sites that pretend to be Twitter, which could result in the inability to access the platform or exposure to malicious content.
Hack Twitter with Spoofing
Spoofing is a technique in which an attacker spoofs identifying information, such as IP addresses, domain names, or email addresses, to impersonate another entity.
Hack Twitter with Hijacking
"Hijacking" is a technique used in the field of computing and computer security in which an individual or a group of individuals take control or usurp control of a resource that does not originally belong to them. This resource can be a computer system, an online session, a user account, a network connection, among others.
In the context of hacking Twitter, hijacking could involve compromising a user's login credentials (through phishing, brute force, or other means) or exploiting a vulnerability in the platform to take control of a legitimate account. Once the attacker has access to the compromised account, they can publish and dispose of the account
How to protect your Twitter account?
- 🔐 Enable two-factor authentication (2FA) on your Twitter account. 2FA adds an extra layer of security by requiring a second verification method in addition to your password to access your account.
- 🔐 Consider using a reliable password manager to generate and manage unique passwords for each account.
- 🔐 Remove unnecessary apps and browser extensions to reduce the potential attack surface on your devices.
- 🔐 Stay alert for suspicious messages and content. Avoid providing personal or financial information in response to suspicious emails, messages, or websites.
- 🔐 Use security tools built into your browser and email to identify and report potential threats










